Generate New Ssl Key Ec2

Step 2: Add Your Key to Your Amazon EC2 Instance. Use the following command to copy your key to your Amazon EC2 instance. /you/.ssh/idrsa.pub is the location to your ssh key, pemfile.pem is the.pem file you normally use to login, and user@ec2-instance.com is the user and hostname to your EC2 instance.
[ aws . ec2 ]
- Turns out that Amazon does not provide ssl certificates for their EC2 instances out of box. I skipped the part that they are a virtual servers providers. To install ssl certificate even the basic one, you need to buy it from someone and install it manually on your server. I used startssl.com They provide free basic ssl certificates.
- The simplest way to generate a key pair is to run ssh-keygen without arguments. In this case, it will prompt for the file in which to store keys. Here's an example: klar (11:39) ssh-keygen Generating public/private rsa key pair.
Description¶
Creates a 2048-bit RSA key pair with the specified name. Amazon EC2 stores the public key and displays the private key for you to save to a file. The private key is returned as an unencrypted PEM encoded PKCS#1 private key. If a key with the specified name already exists, Amazon EC2 returns an error.
You can have up to five thousand key pairs per Region.
The key pair returned to you is available only in the Region in which you create it. If you prefer, you can create your own key pair using a third-party tool and upload it to any Region using ImportKeyPair .
For more information, see Key Pairs in the Amazon Elastic Compute Cloud User Guide .
See also: AWS API Documentation
See 'aws help' for descriptions of global parameters.
Synopsis¶
Options¶
--key-name (string)
A unique name for the key pair.
Constraints: Up to 255 ASCII characters
--dry-run | --no-dry-run (boolean)
--cli-input-json (string)Performs service operation based on the JSON string provided. The JSON string follows the format provided by --generate-cli-skeleton. If other arguments are provided on the command line, the CLI values will override the JSON-provided values. It is not possible to pass arbitrary binary values using a JSON-provided value as the string will be taken literally.
--generate-cli-skeleton (string)Prints a JSON skeleton to standard output without sending an API request. If provided with no value or the value input, prints a sample input JSON that can be used as an argument for --cli-input-json. If provided with the value output, it validates the command inputs and returns a sample output JSON for that command.
See 'aws help' for descriptions of global parameters.
Examples¶
To create a key pair
This example creates a key pair named MyKeyPair.
Command:
The output is an ASCII version of the private key and key fingerprint. You need to save the key to a file.
For more information, see Using Key Pairs in the AWS Command Line Interface User Guide.
Output¶
KeyFingerprint -> (string)
KeyMaterial -> (string)
How To Generate Ssl
KeyName -> (string)
KeyPairId -> (string)
Replace username with your user name, such as ec2-user. You can enter the default user name, or enter a custom user name, if one was previously set up for the instance. For a list of default user names, see General Prerequisites for Connecting to Your Instance.
Replace PublicKeypair with the public key retrieved in step 2. Be sure to enter the entire public key, starting with ssh-rsa.
7. Choose Save.
8. Start your instance.
9. After the cloud-init phase is complete, validate that the public key was replaced.
Important: Because the script contains a key pair, remove the script from the User Data field.
10. Stop your instance.

11. Choose Actions, Instance Settings, and then choose View/Change User Data.
12. Delete all the text in the View/Change User Data dialog box, and then choose Save.
13. Start your instance.
Note: If your instance is Amazon Linux 2 2.0.20190618 or later, you can use EC2 Instance Connect to connect to the instance.
Method 2: Use AWS Systems Manager
If your unreachable instance is listed in AWS Systems Manager as a managed instance, you can use the AWSSupport-ResetAccess document to recover from a lost key pair scenario. This Automation document uses the EC2Rescue for Linux tool on the specified EC2 instance to automatically generate and add a new SSH (Public/Private) key pair.
The new SSH private key for your instance is encrypted and saved in the Parameter Store. The parameter name is /ec2rl/openssh/instance_id/key. Create a new .pem file with this parameter's value as its content and use it to connect back to your unreachable instance.
Note: The Automation workflow creates a backup, password-enabled Amazon Machine Image (AMI). The new AMI is not automatically deleted and remains in your account.

To locate these AMIs:
Generate New Ssl Key Ec2 Download
1. Open the Amazon EC2 console, and then choose AMIs.
Generate Ssl Public Key
2. Enter the Automation execution ID in the search field.

Call Of Duty 1 Multiplayer Cd Key Generator

Installing Call of Duty 2 on Windows 10 has two issues: CD Key is not added to the windows registry during instalation process, and the path to the registry key containing cd-key is different. Here's the FIX: 1) Install Call of Duty 2 on older system. Call of Duty Advanced Warfare Key Generator Screenshot. We present to you the new and updated Call of Duty Advanced Warfare Key Generator. The Key Generator is simple, 100% clean and safe, virus free, works smoothly without any problems at all, updated weekly, all the keys are valid and unique.
Call of Duty Advanced Warfare Activation key generates keys for the latest game “Call of duty Advanced Warfare ” The manufacturer of the program is to programmer “GENIUX.”
Call of Duty Advanced Warfare CD Key Generator
Now you cand download activated Call of Duty Advanced Warfare CD Key Generator from KeyCheats.com Website
Call Of Duty Multiplayer Free
Call of Duty Advanced Warfare CD Key Generator Working
Call of Duty Advanced Warfare has caused a lot of tension from how anticipated it is. Now that an official release date has been given to the public, millions of fans are looking for Call of Duty Advanced Warfare CD key generators in order to play Call of Duty Advanced Warfare CD Key for free.
Call of Duty Advanced Warfare CD Key Generator
Call of Duty Advanced Warfare CD Key Generator for Steam is now available to download. Only our NEW Call of Duty Advanced Warfare Key Generator is working out there. I know there are a lot of fake generators which doesn’t do anything and some viruses are also attached with them but our generators are 100% safe and spyware free.
Call of Duty Advanced Warfare is also a multiplayer game in which you can play online for free with our giveaway cd keys.
– After Download open Call of Duty Advanced Warfare Key Generator and click on the “Generate” button to get your activation code for the PC game Call of Duty Advanced Warfare.
-Then copy this code and when game activation window will appears just insert this key and enjoy the game!
If the key is not correct in the first time, just press the “Generate” button again, do this until the code will be correct!
A permanent Internet Connection is required in the process of code generation! –
We are extremely happy that we can share it with you. We worked on this CD Key really hard, so in return we expect you to appreciate our work. It was really hard to break the codes and access the main game components but our team of professional coders have finally did it.
Guide to download Call of Duty Advanced Warfare CD Key Generator using your Windows, Mac, iOS or Android device:
A few Instructions on Call of Duty Modern Warfare 3 Crack :
- 1. To start with to download Call of Duty Modern Warfare 3 split and initiation key generator for nothing, please take after the directions beneath.
- 2. You should tap on “Produce” catch and after that you will have a free initiation key for Call of Duty Modern Warfare 3 amusement.
- 3. Reorder that Call of Duty Modern Warfare 3 actuation key produced from Call of Duty Modern Warfare 3 split to enactment window of Call of Duty Modern Warfare 3 amusement initiation settings.
- 4. Subsequent to downloading the compressed record beneath, you will get a full instructional guide on the most proficient method to download Call of Duty Modern Warfare 3 diversion for nothing and break it.
- 5. You will likewise have a guide on the best way to split Call of Duty Modern Warfare 3 diversion and how to get initiation key of Call of Duty Modern Warfare 3 for nothing.
- 6. You might be request restart your PC in the wake of breaking Call of Duty Modern Warfare 3 amusement so you can have full access to the diversion with the assistance of Call of Duty Modern Warfare 3 enactment key generator device for nothing.
- 7. You should need to get associated with web at the season of creating the actuation key for Call of Duty Modern Warfare 3 for nothing.
Call of Duty: Modern Warfare 3 Activation Key Generator and Crack
Obligation at hand Modern Warfare 3 break is the 2011 discharge in the top of the line Call of Duty First-Person Shooter activity arrangement. The amusement is an immediate spin-off of the past diversion in the arrangement, Call of Duty: Modern Warfare 2, with a crusade storyline proceeding with the battle of U.S. powers against an intrusion by the Russian Federation following the encircling of a covert U.S. specialist in a fear monger assault on Moscow. Alongside great Call of Duty multi-character control, Call of Duty: Modern Warfare 3 contains profound multiplayer bolster, including two-player Co-operation Survival mode. The diversion additionally contains all-new Kill Streak classes and adjustable strike bundles that offer more alternatives for player battle styles and methodologies. Download Call of Duty Modern Warfare 3 break for nothing just by our group.
Now you cand download activated Call of Duty: Modern Warfare 3 Activation Key Generator and Crack from HackApparatus.com Website
⇓ DOWNLOAD MIRROR 3 ⇓
 ⇓ DOWNLOAD MIRROR 1 ⇓
⇓ DOWNLOAD MIRROR 1 ⇓Call Of Duty 1 Multiplayer Cd Key Generator 2017
⇓ DOWNLOAD MIRROR 2 ⇓Call Of Duty Multiplayer Reveal
Guide to download Call of Duty: Modern Warfare 3 Activation Key Generator and Crack using your Windows, Mac, iOS or Android device:

Generate Ca Private Key Openssl

-->
- Advantages Of Private Key Encryption
- Openssl Create Private Certificate
- Generate Private Key Openssl
- Generate Ca Private Key Openssl Free
Advantages Of Private Key Encryption
The Application Gateway v2 SKU introduces the use of Trusted Root Certificates to allow backend servers. This removes authentication certificates that were required in the v1 SKU. The root certificate is a Base-64 encoded X.509(.CER) format root certificate from the backend certificate server. It identifies the root certificate authority (CA) that issued the server certificate and the server certificate is then used for the TLS/SSL communication.
- Oct 25, 2019 To prove ownership of the private key, the CSR is signed with the subject's private key. Generate a CSR: $ openssl req -new -key example.org.key -out example.org.csr You are about to be asked to enter information that will be.
- Create a PKCS#12 keystore from a private key and certificate. OpenSSL is an open source software library that provides the pkcs12 command for generating PKCS#12 files from a private key and a certificate.
Run the following OpenSSL command to generate your private key and public certificate. Answer the questions and enter the Common Name when prompted. Openssl req -newkey rsa:2048 -nodes -keyout key.pem -x509 -days 365 -out certificate.pem.
Application Gateway trusts your website's certificate by default if it's signed by a well-known CA (for example, GoDaddy or DigiCert). You don't need to explicitly upload the root certificate in that case. For more information, see Overview of TLS termination and end to end TLS with Application Gateway. However, if you have a dev/test environment and don't want to purchase a verified CA signed certificate, you can create your own custom CA and create a self-signed certificate with it.
Note
Self-signed certificates are not trusted by default and they can be difficult to maintain. Also, they may use outdated hash and cipher suites that may not be strong. For better security, purchase a certificate signed by a well-known certificate authority.
In this article, you will learn how to:
- Create your own custom Certificate Authority
- Create a self-signed certificate signed by your custom CA
- Upload a self-signed root certificate to an Application Gateway to authenticate the backend server
Prerequisites
OpenSSL on a computer running Windows or Linux
While there could be other tools available for certificate management, this tutorial uses OpenSSL. You can find OpenSSL bundled with many Linux distributions, such as Ubuntu.
A web server
For example, Apache, IIS, or NGINX to test the certificates.
An Application Gateway v2 SKU
If you don't have an existing application gateway, see Quickstart: Direct web traffic with Azure Application Gateway - Azure portal.
Create a root CA certificate
Create your root CA certificate using OpenSSL.
Create the root key
Sign in to your computer where OpenSSL is installed and run the following command. This creates a password protected key.
At the prompt, type a strong password. For example, at least nine characters, using upper case, lower case, numbers, and symbols.
Create a Root Certificate and self-sign it
Use the following commands to generate the csr and the certificate.
The previous commands create the root certificate. You'll use this to sign your server certificate.
When prompted, type the password for the root key, and the organizational information for the custom CA such as Country, State, Org, OU, and the fully qualified domain name (this is the domain of the issuer).
Create a server certificate
Next, you'll create a server certificate using OpenSSL.
Create the certificate's key
Use the following command to generate the key for the server certificate.
Create the CSR (Certificate Signing Request)
The CSR is a public key that is given to a CA when requesting a certificate. The CA issues the certificate for this specific request.
Note
The CN (Common Name) for the server certificate must be different from the issuer's domain. For example, in this case, the CN for the issuer is www.contoso.com and the server certificate's CN is www.fabrikam.com.
Use the following command to generate the CSR:
When prompted, type the password for the root key, and the organizational information for the custom CA: Country, State, Org, OU, and the fully qualified domain name. This is the domain of the website and it should be different from the issuer.
Openssl Create Private Certificate
Generate the certificate with the CSR and the key and sign it with the CA's root key
Use the following command to create the certificate:
Verify the newly created certificate
Use the following command to print the output of the CRT file and verify its content:
Verify the files in your directory, and ensure you have the following files:
- contoso.crt
- contoso.key
- fabrikam.crt
- fabrikam.key
Configure the certificate in your web server's TLS settings
In your web server, configure TLS using the fabrikam.crt and fabrikam.key files. If your web server can't take two files, you can combine them to a single .pem or .pfx file using OpenSSL commands.
IIS
For instructions on how to import certificate and upload them as server certificate on IIS, see HOW TO: Install Imported Certificates on a Web Server in Windows Server 2003.
For TLS binding instructions, see How to Set Up SSL on IIS 7.
Apache
The following configuration is an example virtual host configured for SSL in Apache:
NGINX
The following configuration is an example NGINX server block with TLS configuration:
Access the server to verify the configuration
Add the root certificate to your machine's trusted root store. When you access the website, ensure the entire certificate chain is seen in the browser.
Note
It's assumed that DNS has been configured to point the web server name (in this example, www.fabrikam.com) to your web server's IP address. If not, you can edit the hosts file to resolve the name.
Browse to your website, and click the lock icon on your browser's address box to verify the site and certificate information.
Verify the configuration with OpenSSL
Or, you can use OpenSSL to verify the certificate.
Upload the root certificate to Application Gateway's HTTP Settings
To upload the certificate in Application Gateway, you must export the .crt certificate into a .cer format Base-64 encoded. Since .crt already contains the public key in the base-64 encoded format, just rename the file extension from .crt to .cer.
Azure portal
To upload the trusted root certificate from the portal, select the HTTP Settings and choose the HTTPS protocol.
Azure PowerShell
Or, you can use Azure CLI or Azure PowerShell to upload the root certificate. The following code is an Azure PowerShell sample.
Note
The following sample adds a trusted root certificate to the application gateway, creates a new HTTP setting and adds a new rule, assuming the backend pool and the listener exist already.
Verify the application gateway backend health
- Click the Backend Health view of your application gateway to check if the probe is healthy.
- You should see that the Status is Healthy for the HTTPS probe.
Next steps
To learn more about SSLTLS in Application Gateway, see Overview of TLS termination and end to end TLS with Application Gateway.
While Encrypting a File with a Password from the Command Line using OpenSSLis very useful in its own right, the real power of the OpenSSL library is itsability to support the use of public key cryptograph for encrypting orvalidating data in an unattended manner (where the password is not required toencrypt) is done with public keys.
The Commands to Run
Generate a 2048 bit RSA Key
You can generate a public and private RSA key pair like this:
openssl genrsa -des3 -out private.pem 2048
That generates a 2048-bit RSA key pair, encrypts them with a password you provideand writes them to a file. You need to next extract the public key file. You willuse this, for instance, on your web server to encrypt content so that it canonly be read with the private key.
Export the RSA Public Key to a File
This is a command that is
openssl rsa -in private.pem -outform PEM -pubout -out public.pem
The -pubout flag is really important. Be sure to include it.
Next open the public.pem and ensure that it starts with-----BEGIN PUBLIC KEY-----. This is how you know that this file is thepublic key of the pair and not a private key.

To check the file from the command line you can use the less command, like this:
less public.pem
Do Not Run This, it Exports the Private Key
A previous version of the post gave this example in error.
openssl rsa -in private.pem -out private_unencrypted.pem -outform PEM
The error is that the -pubout was dropped from the end of the command.That changes the meaning of the command from that of exporting the public keyto exporting the private key outside of its encrypted wrapper. Inspecting theoutput file, in this case private_unencrypted.pem clearly shows that the keyis a RSA private key as it starts with -----BEGIN RSA PRIVATE KEY-----.
Visually Inspect Your Key Files
It is important to visually inspect you private and public key files to makesure that they are what you expect. OpenSSL will clearly explain the nature ofthe key block with a -----BEGIN RSA PRIVATE KEY----- or -----BEGIN PUBLIC KEY-----.
You can use less to inspect each of your two files in turn:
less private.pemto verify that it starts with a-----BEGIN RSA PRIVATE KEY-----less public.pemto verify that it starts with a-----BEGIN PUBLIC KEY-----
The next section shows a full example of what each key file should look like.
Generate Private Key Openssl
The Generated Key Files
The generated files are base64-encoded encryption keys in plain text format.If you select a password for your private key, its file will be encrypted withyour password. Be sure to remember this password or the key pair becomes useless.
The private.pem file looks something like this:
The public key, public.pem, file looks like:
Protecting Your Keys
Depending on the nature of the information you will protect, it’s important tokeep the private key backed up and secret. The public key can be distributedanywhere or embedded in your web application scripts, such as in your PHP,Ruby, or other scripts. Again, backup your keys!
Remember, if the key goes away the data encrypted to it is gone. Keeping aprinted copy of the key material in a sealed envelope in a bank safety depositbox is a good way to protect important keys against loss due to fire or harddrive failure.
Generate Ca Private Key Openssl Free
Oh, and one last thing.
If you, dear reader, were planning any funny business with the private key that I have just published here. Know that they were made especially for this series of blog posts. I do not use them for anything else.
Found an issue?
Rietta plans, develops, and maintains applications.
Learn more about our services or drop us your email and we'll e-mail you back.
Other Blog Articles Published by Rietta.com

Dvdfab 6 Registration Key Generator

DVDFab 11 Full Version Crack With Serial Key
DVDFab 11.0.8.4 Crack is all-in-one DVD software for copying, converting and burning. You can copy any DVD to DVDR, PSP and iPod in just one or two steps easily. It permits you to remove all DVD copy protections like UOPs, CSS, RCE, CPPM, RC, APS, RipGuard, FluxDVD, ARccOS, CORE X2 etc. It is frequently updated to support the newest DVD copy protections and has a very fast copying speed; usually, it is about 10 to 20 minutes. There is no doubt that DVDFab Key is one of the world-famous products devoted to work on multimedia software resolutions for more than 12 years.
DVDFab Crack permits you to copy or double one disk and various circumstances for dispersal. Provides you help to acquire and expose harmful disks. It also provides actually fast processing speed with no compromises on high quality of a video. Furthermore, It also provides a secure interface for all operations without any risk of data damage. It is very simple and very efficient to use. DVDFab With Crack is the best application to compress a double layer of the number of disks on a single layer with just one or two clicks. This program is one of the most demanding and most popular applications in terms of format. It helps you to create DVDs and Blu-ray discs. You can use DVDFab to accomplish your DVDs in a modest way.
Nov 22, 2019 DVDFab Passkey 9.3.6.1 Registration Key Generator is the advanced version of this program with the latest tools.It supports all media players. Thus, you can use it to manage media. In addition, you can perform different operations such as you can burn, edit, and play. Mar 23, 2020 DVDFab 11.0.8.1 Crack + Registration Key 2020 Final Keygen Latest. DVDFab 11 Crack is an exceptional expert and amazing asset for you to effortlessly duplicate, reinforcement, copy or clone any DVD the manner in which you need. 6 duplicate modes accessible for you to deftly do what you need, and they’re Full Disk, Main Movie, Customize, Split, Merge and Clone/Burn.
Apr 02, 2020 DVDFab 11 Crack 2020 With Serial Key Full Version Free Download. DVDFab 11.0.8.4 Crack a powerful software for DVDs as all of its features are associated with the DVDs. Users can convert, barn, and copy the data using this software. Users can remove several DVD copy protections such as CORE x2, CPPM, CSS, RCE, FluxDVD, RC, RipGuard, APS, UOPs, and ARccOS. Mar 26, 2020 DVDFab 11.0.8.1 Keygen Full Serial Key Final Patch Mac Win More, DVDFab MAC Crack is a very well composed and useful tool, which scans all mainstream video positions from the Internet and converts them to a PC for numerous characters.
DVDFab is a combined shareware bundle that includes DVDFab DVD Copy, DVDFab Blu-ray Ripper, DVDFab DVD Ripper, DVDFab Blu-ray Copy, and DVDFab Blu-ray 3D Ripper, DVDFab 2D to 3D Converter, DVDFab Video Converter, DVD Creator, Blu-ray Creator, DVDFab Blu-ray to DVD Converter and DVDFab File Transfer. It is the finest software with proficient tools.
DVDFab Crack Full Version Keygen Free Download
DVDFab keygen is one of the most expedient, efficient and environmentally friendly disk processing apps. You can use DVDFab to create a bootable USB or flash that can be used for booting system from a crash. This program is one of the best recovery programs of any broken disk type. It is hard to find the right useful application on Google so, I recommend you to download this application and try it at least once then you will know that this is the best among all other applications. DVDFab Full Version is the finest program for skillful customers and always provides you a safe, secure, best and higher result.
This software is compatible with almost all Windows Operating Systems and also with Mac devices. This is the best software you can use to save your time and work efficiently.
DVDFab Key Features :

- This application can create a backup of your system easily.
- To create multi-source disks, it merges more than on one disk image.
- Convert DVD to iPod, Archos (and other PVPs), Zune, PSP, XboX360, Cell Phone, PDA or mobile devices and resize images to well suit your player.
- You can also choose to convert audio only to sort MP3s from DVD audio streams.
- It has a safe interface for all the processes without the threat of any data damage.
- Moreover, It allows you to copy all kind of data such as menus, movies and trailers and can add a different type of images and backgrounds.
- You can alter your videos into any format because it provides you an enormous list of formats.
- The double-layered disc can split easily.
- Also, this software is advance DVD managing software and can burn any blank DVD disk easily.
- For data recovery, DVDFab 11 Crack is the best for you.
- You can organize multiple tasks as you can duplicate and burn discs.
- Also, it work simply and smoothly because it is lightweight software.
- Furthermore, You can copy the identical/duplicate data that you inscribe to entirely different disks.
- For any movie, you can also select the sound.
- in Addition, New template disk and folder can create in it.
- The speed of copying is very fast.
- Furthermore, All the data can copy in a few minutes.
People also Download: Smadav Pro Antivirus
What is new in DVDFab 11 Crack?
- New interface and more effective features added.
- The feature of watermark removal is available now.
- For the user of all over the world, it supports multiple languages.
- The support added for some new Java protections.
- Old installed version automatically removes when the new version is installed.
- Moreover Support added for the Latest iOS version.
- Modest in consumption for the new user.
System Requirements:
- Windows 8, 8.1, 10 and Vista.
- 7 – 10.12 for Mac.
- Pentium at least II with 500 MHz.
- For DVD, minimum RAM of 256 MB and 10 GB of free hard disk space.
- For Blu-Ray, minimum RAM of 512 MB and 50 GB of free hard disk space.
- Internet connection to use it.
DVDFab 11 Serial Keys Updated {2020}:
- PDH37-2BD7F-BWOQG-E7EJV-RIDHS-
- HEUEO-QVSKD-ODGW8-SBS7W-O2VGS
- YDBWO-QYSKS-OWBEY-SBDU2-3YSVS
How to install DVDFab Full Version Free:
- First of all, Download the setup of DVDFab Crack.
- Now install DVDFab Cracked File.
- Close the program, after installation.
- Then, Run it.
- Password is Cracksmod
- Copy the file and replace it.
- Open keygen after that.
- Press active now and wait.
- Finally, Done, now enjoy it.
Dvdfab 10 Activation Key
Dvdfab 6 Registration Key Code
Dvdfab 6 Registration Key Generator 2017

Pgp Generate Public Key From Private Key

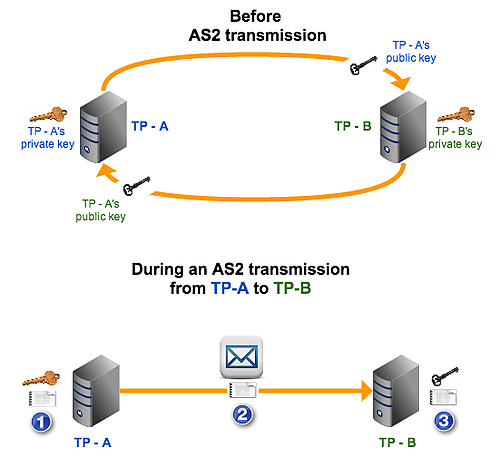
Encryption is a process of embedding plain text data in such a way that it cannot be decoded by outsiders. It is necessary to encrypt data to prevent misuse. The GNU Privacy Guard (GPG) application allows you to encrypt and decrypt information. It is based on the use of a pair of keys, one public and one private (or secret). Data encrypted with one key can only be decrypted with the other. To encrypt a message to you, someone would use your public key to create a message that could only be unlocked with your private key. To sign information, you would lock it with your private key, allowing anyone to verify that it came from you by unlocking it with your public key.
Pretty Good Privacy (PGP) provides data encryption and decryption for communication data such as texts, emails, directories, and files. It uses a algorithmic combination of hashing, data compression, symmetric-key cryptography, and public-key cryptography to sign, encrypt, and decrypt messages using a combination of private and public cryptographic keys. Aug 17, 2017 use this online tool igolder to generate key pair keep the private key with you and share the public key with third party, but do remember the password which you provide in that website while generating that key pair you need that one in module configuration check this blog for more details on PGP. Look to Subj: How to get public key from private in gpg without using local storage (under /.gpg)? Browse other questions tagged pgp gnupg or ask your own question. Generate gpg public and private keys without any interaction. May 28, 2015 This blog describes how to generate a private/public key pair using GPG version 1.4.5. The resulting public key will contain two keys, one key for signing and a subkey for encryption. This key can be used with HCM Fusion SaaS to encrypt/decrypt files as they are transferred to.
Modern Linux distributions have gpg already installed on them. If not present, install it.
on Centos
on Ubuntu
1) Create gpg key
Generate Ssh Public Key From Private Key
When installing gnupg package, we need to understand the concept to use gpg as well.
Generating a new keypair
To encrypt your communication, the first thing to do is to create a new keypair. GPG is able to create several types of keypairs, but a primary key must be capable of making signatures.
uid:Please take a note about the USER-ID mentioned in the result. We will use its value to do some operation.pub:It represents the public key. The key-id is BAC361F1. Yours will be differentsub:It represents subkeys, goes along with the primary key. Commonly, it is used to encryption.
Your prompt can be handled for a very long time without finishing if you see the message below
'Not enough random bytes available. Please do some other work to give
the OS a chance to collect more entropy! (Need 285 more bytes)'
The problem is caused by the lack of entropy (or random system noise). So cancel the process and check the available entropy
You can see it is not enough. We can install a package to solve the lack of entropy with rngd which is a random number generator utility used to check immediately the available entropy
Now can start again with the gpg --gen-key command and the process will be fine. We have only installed it without anything else. In certain distributions, you need to use rngd before the gpg process.
3) Generating a revocation certificate
After your keypair is created you should immediately generate a revocation certificate to revoke your public key if your private key has been compromised in any way or if you lose it. Create it when you create your key. The process requires your private key, passphrase.
The argument BAC361F1 is the key ID. It must be a key specifier, either the key ID of your primary keypair or any part of a user ID that identifies your keypair like my_name@linoxide.com. The generated certificate will be saved in revoke_key.asc file. Store it where others can't access it because anybody having access to it can revoke your key, rendering it useless. If the --output option is omitted, the result will be placed on standard output.

4) Making an ASCII armored version of your public key
Pgp Generate Public Key From Private Key Code
Some keyservers allow you to paste an ASCII armored version of your public key in order to upload it directly. This method is most preferred because the key comes directly from the user who can see that the key has been successfully uploaded.
5) Exchanging keys
In order to communicate with others, you must exchange public keys. To do it, you must be able to list your keys. There is some commands to list your public keyring
gpg --list-keys:List all keys from the public keyrings, or just the keys given on the command line.gpg --list-secret-keys:List all keys from the secret keyrings or just the ones given on the command linegpg --list-sigs:Same as --list-keys, but the signatures are listed too.
Export a public key
Now that you have generated a key pair, the next step is to publish your public key on internet ( Keyservers ) so that other person can use it to send you a message. You can use either the key ID or any part of the user ID may be used to identify the key to export. There are two commands but with the first command, the key is exported in a binary format and can be inconvenient when it is sent through email or published on a web page. So, we will use the second command for ASCII armored method.
The output will be redirected to my_pubkey.gpg file which has the content of the public key to provide for communication.
Submit your public keys to a keyserver
Once you have this ASCII-armored public key, you can manually paste it into a form at a public key server like pgp.mit.edu
Because someone seems to have sent you their public key, there's no reason to trust that it's from that person unless you have validated it.
Import a public key
As others persons can use your public key to send you a message, you can import public from people you trust in to communicate with them.
Conclusion
Now we have notions on the principles to use and generate a public key. You know how GnuPG is functioning and you can use it for secure communication. GPG encryption is only useful when both parties use good security practices and are vigilant.
Symmetric Key
Read Also:

Rsa Key Generation In Javascript

How I create RSA key and enable SSH access in Cisco VG202, in a Cisco router I use the next commands(but in a VG not exists): conf t crypto key generate rsa modulus 1024 ip domain-name domain-name ip ssh version 2 ip ssh time-out 120 ip ssh. Generating a new SSH key. Open Terminal Terminal Git Bash. Paste the text below, substituting in your GitHub email address. $ ssh-keygen -t rsa -b 4096 -C 'youremail@example.com' This creates a new ssh key, using the provided email as a label. Generating public/private rsa key pair.
-->Creating and managing keys is an important part of the cryptographic process. Symmetric algorithms require the creation of a key and an initialization vector (IV). The key must be kept secret from anyone who should not decrypt your data. The IV does not have to be secret, but should be changed for each session. Asymmetric algorithms require the creation of a public key and a private key. The public key can be made public to anyone, while the private key must known only by the party who will decrypt the data encrypted with the public key. This section describes how to generate and manage keys for both symmetric and asymmetric algorithms.

Symmetric Keys
The symmetric encryption classes supplied by the .NET Framework require a key and a new initialization vector (IV) to encrypt and decrypt data. Whenever you create a new instance of one of the managed symmetric cryptographic classes using the parameterless constructor, a new key and IV are automatically created. Anyone that you allow to decrypt your data must possess the same key and IV and use the same algorithm. Generally, a new key and IV should be created for every session, and neither the key nor IV should be stored for use in a later session.
To communicate a symmetric key and IV to a remote party, you would usually encrypt the symmetric key by using asymmetric encryption. Sending the key across an insecure network without encrypting it is unsafe, because anyone who intercepts the key and IV can then decrypt your data. For more information about exchanging data by using encryption, see Creating a Cryptographic Scheme.
The following example shows the creation of a new instance of the TripleDESCryptoServiceProvider class that implements the TripleDES algorithm.
When the previous code is executed, a new key and IV are generated and placed in the Key and IV properties, respectively.
Sometimes you might need to generate multiple keys. In this situation, you can create a new instance of a class that implements a symmetric algorithm and then create a new key and IV by calling the GenerateKey and GenerateIV methods. The following code example illustrates how to create new keys and IVs after a new instance of the symmetric cryptographic class has been made.
When the previous code is executed, a key and IV are generated when the new instance of TripleDESCryptoServiceProvider is made. Another key and IV are created when the GenerateKey and GenerateIV methods are called.
Asymmetric Keys
The .NET Framework provides the RSACryptoServiceProvider and DSACryptoServiceProvider classes for asymmetric encryption. These classes create a public/private key pair when you use the parameterless constructor to create a new instance. Asymmetric keys can be either stored for use in multiple sessions or generated for one session only. While the public key can be made generally available, the private key should be closely guarded.
A public/private key pair is generated whenever a new instance of an asymmetric algorithm class is created. After a new instance of the class is created, the key information can be extracted using one of two methods:
The ToXmlString method, which returns an XML representation of the key information.
The ExportParameters method, which returns an RSAParameters structure that holds the key information.
Both methods accept a Boolean value that indicates whether to return only the public key information or to return both the public-key and the private-key information. An RSACryptoServiceProvider class can be initialized to the value of an RSAParameters structure by using the ImportParameters method.
Asymmetric private keys should never be stored verbatim or in plain text on the local computer. If you need to store a private key, you should use a key container. For more on how to store a private key in a key container, see How to: Store Asymmetric Keys in a Key Container.
The following code example creates a new instance of the RSACryptoServiceProvider class, creating a public/private key pair, and saves the public key information to an RSAParameters structure.
See also
RSA(Rivest-Shamir-Adleman) is an Asymmetric encryption technique that uses two different keys as public and private keys to perform the encryption and decryption. With RSA, you can encrypt sensitive information with a public key and a matching private key is used to decrypt the encrypted message. Asymmetric encryption is mostly used when there are 2 different endpoints are involved such as VPN client and server, SSH, etc.
Below is an online tool to perform RSA encryption and decryption as a RSA calculator.
For Java implementation of RSA, you can follow this article.
First, we require public and private keys for RSA encryption and decryption. Hence, below is the tool to generate RSA key online. It generates RSA public key as well as the private key of size 512 bit, 1024 bit, 2048 bit, 3072 bit and 4096 bit with Base64 encoded.
By default, the private key is generated in PKCS#8 format and the public key is generated in X.509 format.
Generate RSA Key Online
Public Key
RSA Encryption and Decryption Online
Below is the tool for encryption and decryption. Either you can use the public/private keys generated above or supply your own public/private keys.
Any private or public key value that you enter or we generate is not stored on this site, this tool is provided via an HTTPS URL to ensure that private keys cannot be stolen.
This tool provides flexibility for RSA encrypt with public key as well as private key along with RSA decrypt with public or private key.
If You Appreciate What We Do Here On Devglan, You Can Consider:
- Like us at: or follow us at
- Share this article on social media or with your teammates.
- We are thankful for your never ending support.
Usage Guide - RSA Encryption and Decryption Online
In the first section of this tool, you can generate public or private keys. To do so, select the RSA key size among 515, 1024, 2048 and 4096 bit click on the button. This will generate the keys for you.
For encryption and decryption, enter the plain text and supply the key. As the encryption can be done using both the keys, you need to tell the tool about the key type that you have supplied with the help of radio button. By default, public key is selected. Then, you can use the cipher type to be used for the encryption. The different cipger options are RSA, RSA/ECB/PKCS1Padding and RSA/ECB/OAEPWithSHA-1AndMGF1Padding. Now, once you click the encrypt button the encrypted result will be shown in the textarea just below the button.
Remember, the encrypted result is by default base64 encoded.
Similarly, for decryption the process is same. Here, you need to enter the RSA encrypted text and the result will be a plain-text. You have both options to decrypt the encryption with public and private keys.
References
Rsa Key Generation In Javascript Pdf
Other Free Tools

Generating A Public Key From A Private Key

- Generating A Public Key From A Private Key West
- Generate A Public Key
- Generating A Ssh Key Public/private Key Pair
- Generating A Public Key From A Private Keyboard
Generating A Public Key From A Private Key West
Creating and managing keys is an important part of the cryptographic process. Symmetric algorithms require the creation of a key and an initialization vector (IV). The key must be kept secret from anyone who should not decrypt your data. The IV does not have to be secret, but should be changed for each session. Asymmetric algorithms require the creation of a public key and a private key. The public key can be made public to anyone, while the private key must known only by the party who will decrypt the data encrypted with the public key. This section describes how to generate and manage keys for both symmetric and asymmetric algorithms.
Symmetric Keys
The symmetric encryption classes supplied by the .NET Framework require a key and a new initialization vector (IV) to encrypt and decrypt data. Whenever you create a new instance of one of the managed symmetric cryptographic classes using the parameterless constructor, a new key and IV are automatically created. Anyone that you allow to decrypt your data must possess the same key and IV and use the same algorithm. Generally, a new key and IV should be created for every session, and neither the key nor IV should be stored for use in a later session.
Generating a Public/Private Key Pair. You need to programmatically create a public/private key pair using the RSA algorithm with a minimum key strength of 2048 bits. The method you use to generate this key pair may differ depending on platform and programming language. How to generate public/private key in C#. Asymmetric cryptography also known as public-key encryption uses a public/private key pair to encrypt and decrypt data. In.NET, the RSACryptoServiceProvider and DSACryptoServiceProvider classes are used for asymmetric encryption. Generating Keys for Encryption and Decryption.; 3 minutes to read +7; In this article. Creating and managing keys is an important part of the cryptographic process. Symmetric algorithms require the creation of a key and an initialization vector (IV). The key must be kept secret from anyone who should not decrypt your data.
To communicate a symmetric key and IV to a remote party, you would usually encrypt the symmetric key by using asymmetric encryption. Sending the key across an insecure network without encrypting it is unsafe, because anyone who intercepts the key and IV can then decrypt your data. For more information about exchanging data by using encryption, see Creating a Cryptographic Scheme.
The following example shows the creation of a new instance of the TripleDESCryptoServiceProvider class that implements the TripleDES algorithm.
Generate A Public Key
When the previous code is executed, a new key and IV are generated and placed in the Key and IV properties, respectively.
Sometimes you might need to generate multiple keys. In this situation, you can create a new instance of a class that implements a symmetric algorithm and then create a new key and IV by calling the GenerateKey and GenerateIV methods. The following code example illustrates how to create new keys and IVs after a new instance of the symmetric cryptographic class has been made.
When the previous code is executed, a key and IV are generated when the new instance of TripleDESCryptoServiceProvider is made. Another key and IV are created when the GenerateKey and GenerateIV methods are called.
Asymmetric Keys
The .NET Framework provides the RSACryptoServiceProvider and DSACryptoServiceProvider classes for asymmetric encryption. These classes create a public/private key pair when you use the parameterless constructor to create a new instance. Asymmetric keys can be either stored for use in multiple sessions or generated for one session only. While the public key can be made generally available, the private key should be closely guarded.
A public/private key pair is generated whenever a new instance of an asymmetric algorithm class is created. After a new instance of the class is created, the key information can be extracted using one of two methods:
The ToXmlString method, which returns an XML representation of the key information.
The ExportParameters method, which returns an RSAParameters structure that holds the key information.
Both methods accept a Boolean value that indicates whether to return only the public key information or to return both the public-key and the private-key information. An RSACryptoServiceProvider class can be initialized to the value of an RSAParameters structure by using the ImportParameters method.
Asymmetric private keys should never be stored verbatim or in plain text on the local computer. If you need to store a private key, you should use a key container. For more on how to store a private key in a key container, see How to: Store Asymmetric Keys in a Key Container.
Generating A Ssh Key Public/private Key Pair
The following code example creates a new instance of the RSACryptoServiceProvider class, creating a public/private key pair, and saves the public key information to an RSAParameters structure.
Generating A Public Key From A Private Keyboard
See also
