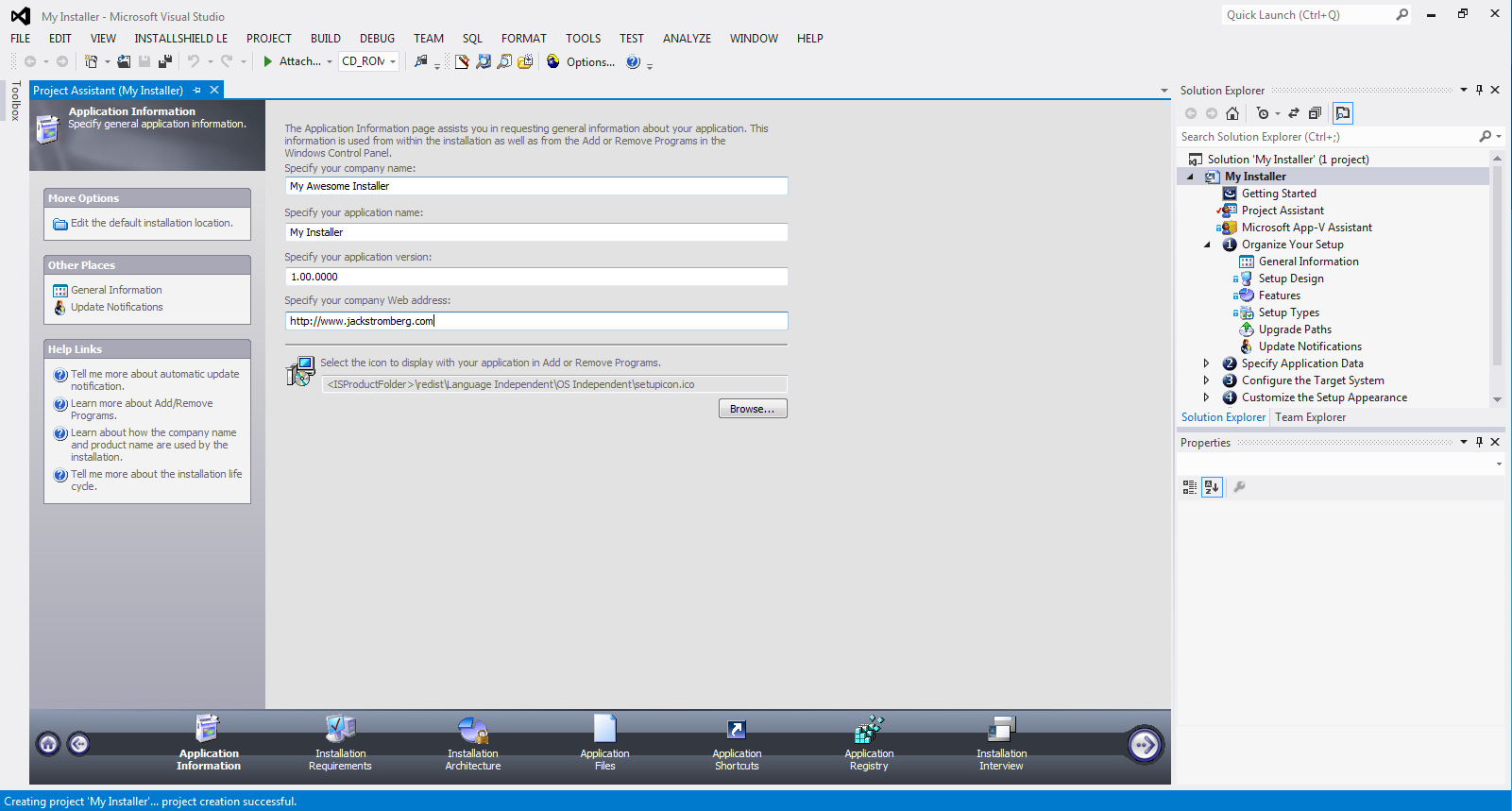
Generate Dsa Key Ssh Keygen

Generate an RSA SSH keypair with a 4096 bit private key. Ssh-keygen -t rsa -b 4096 -C 'RSA 4096 bit Keys'. Generate an DSA SSH keypair with a 2048 bit private key. Ssh-keygen -t dsa -b 1024 -C 'DSA 1024 bit Keys'. Generate an ECDSA SSH keypair with a 521 bit private key. A SSH private key as generated by ssh-keygen contains a public key part. How do I retrieve this public key from the private key? How do I retrieve this public key from the private key? I've lost my public key and need to put the contents of this public key in the servers authorizedkeys file and do not want to create a new key pair. Enabling DSA key-based authentication on UNIX and Linux operating systems Use the ssh-keygen tool to create a key pair. Log in as the administrator user defined on the service form. Start the ssh-keygen tool.
This article or section needs expansion.
SSH keys can serve as a means of identifying yourself to an SSH server using public-key cryptography and challenge-response authentication. The major advantage of key-based authentication is that in contrast to password authentication it is not prone to brute-force attacks and you do not expose valid credentials, if the server has been compromised.[1]
Furthermore SSH key authentication can be more convenient than the more traditional password authentication. When used with a program known as an SSH agent, SSH keys can allow you to connect to a server, or multiple servers, without having to remember or enter your password for each system.

Key-based authentication is not without its drawbacks and may not be appropriate for all environments, but in many circumstances it can offer some strong advantages. A general understanding of how SSH keys work will help you decide how and when to use them to meet your needs.
This article assumes you already have a basic understanding of the Secure Shell protocol and have installed the openssh package.
- 2Generating an SSH key pair
- 2.1Choosing the authentication key type
- 2.2Choosing the key location and passphrase
- 3Copying the public key to the remote server
- 4SSH agents
- 4.1ssh-agent
- 4.3Keychain
- 4.4x11-ssh-askpass
- 4.5pam_ssh
- 5Troubleshooting
Background
SSH keys are always generated in pairs with one known as the private key and the other as the public key. The private key is known only to you and it should be safely guarded. By contrast, the public key can be shared freely with any SSH server to which you wish to connect.
If an SSH server has your public key on file and sees you requesting a connection, it uses your public key to construct and send you a challenge. This challenge is an encrypted message and it must be met with the appropriate response before the server will grant you access. What makes this coded message particularly secure is that it can only be understood by the private key holder. While the public key can be used to encrypt the message, it cannot be used to decrypt that very same message. Only you, the holder of the private key, will be able to correctly understand the challenge and produce the proper response.
This challenge-response phase happens behind the scenes and is invisible to the user. As long as you hold the private key, which is typically stored in the ~/.ssh/ directory, your SSH client should be able to reply with the appropriate response to the server.
A private key is a guarded secret and as such it is advisable to store it on disk in an encrypted form. When the encrypted private key is required, a passphrase must first be entered in order to decrypt it. While this might superficially appear as though you are providing a login password to the SSH server, the passphrase is only used to decrypt the private key on the local system. The passphrase is not transmitted over the network.
Generating an SSH key pair
An SSH key pair can be generated by running the ssh-keygen command, defaulting to 3072-bit RSA (and SHA256) which the ssh-keygen(1) man page says is 'generally considered sufficient' and should be compatible with virtually all clients and servers:
The randomart image was introduced in OpenSSH 5.1 as an easier means of visually identifying the key fingerprint.
-a switch to specify the number of KDF rounds on the password encryption.You can also add an optional comment field to the public key with the -C switch, to more easily identify it in places such as ~/.ssh/known_hosts, ~/.ssh/authorized_keys and ssh-add -L output. For example:
will add a comment saying which user created the key on which machine and when.
Choosing the authentication key type
OpenSSH supports several signing algorithms (for authentication keys) which can be divided in two groups depending on the mathematical properties they exploit:
- DSA and RSA, which rely on the practical difficulty of factoring the product of two large prime numbers,
- ECDSA and Ed25519, which rely on the elliptic curve discrete logarithm problem. (example)
Elliptic curve cryptography (ECC) algorithms are a more recent addition to public key cryptosystems. One of their main advantages is their ability to provide the same level of security with smaller keys, which makes for less computationally intensive operations (i.e. faster key creation, encryption and decryption) and reduced storage and transmission requirements.
OpenSSH 7.0 deprecated and disabled support for DSA keys due to discovered vulnerabilities, therefore the choice of cryptosystem lies within RSA or one of the two types of ECC.
#RSA keys will give you the greatest portability, while #Ed25519 will give you the best security but requires recent versions of client & server[2][dead link 2020-04-02 ⓘ]. #ECDSA is likely more compatible than Ed25519 (though still less than RSA), but suspicions exist about its security (see below).
RSA
ssh-keygen defaults to RSA therefore there is no need to specify it with the -t option. It provides the best compatibility of all algorithms but requires the key size to be larger to provide sufficient security.
Minimum key size is 1024 bits, default is 3072 (see ssh-keygen(1)) and maximum is 16384.
If you wish to generate a stronger RSA key pair (e.g. to guard against cutting-edge or unknown attacks and more sophisticated attackers), simply specify the -b option with a higher bit value than the default:
Be aware though that there are diminishing returns in using longer keys.[3][4] The GnuPG FAQ reads: 'If you need more security than RSA-2048 offers, the way to go would be to switch to elliptical curve cryptography — not to continue using RSA'.[5]
On the other hand, the latest iteration of the NSA Fact Sheet Suite B Cryptography[dead link 2020-04-02 ⓘ] suggests a minimum 3072-bit modulus for RSA while '[preparing] for the upcoming quantum resistant algorithm transition'.[6]
ECDSA
The Elliptic Curve Digital Signature Algorithm (ECDSA) was introduced as the preferred algorithm for authentication in OpenSSH 5.7. Some vendors also disable the required implementations due to potential patent issues.
Ssh Keygen For Ssh
There are two sorts of concerns with it:
- Political concerns, the trustworthiness of NIST-produced curves being questioned after revelations that the NSA willingly inserts backdoors into softwares, hardware components and published standards were made; well-known cryptographers haveexpresseddoubts about how the NIST curves were designed, and voluntary tainting has already beenproved in the past.
- Technical concerns, about the difficulty to properly implement the standard and the slowness and design flaws which reduce security in insufficiently precautious implementations.
Both of those concerns are best summarized in libssh curve25519 introduction. Although the political concerns are still subject to debate, there is a clear consensus that #Ed25519 is technically superior and should therefore be preferred.
Ed25519
Ed25519 was introduced in OpenSSH 6.5 of January 2014: 'Ed25519 is an elliptic curve signature scheme that offers better security than ECDSA and DSA and good performance'. Its main strengths are its speed, its constant-time run time (and resistance against side-channel attacks), and its lack of nebulous hard-coded constants.[7] See also this blog post by a Mozilla developer on how it works.
It is already implemented in many applications and libraries and is the default key exchange algorithm (which is different from key signature) in OpenSSH.
Ed25519 key pairs can be generated with:
Generate Dsa Key Ssh Keygen Download
There is no need to set the key size, as all Ed25519 keys are 256 bits.
Keep in mind that older SSH clients and servers may not support these keys.
Choosing the key location and passphrase
Upon issuing the ssh-keygen command, you will be prompted for the desired name and location of your private key. By default, keys are stored in the ~/.ssh/ directory and named according to the type of encryption used. You are advised to accept the default name and location in order for later code examples in this article to work properly.
When prompted for a passphrase, choose something that will be hard to guess if you have the security of your private key in mind. A longer, more random password will generally be stronger and harder to crack should it fall into the wrong hands.
It is also possible to create your private key without a passphrase. While this can be convenient, you need to be aware of the associated risks. Without a passphrase, your private key will be stored on disk in an unencrypted form. Anyone who gains access to your private key file will then be able to assume your identity on any SSH server to which you connect using key-based authentication. Furthermore, without a passphrase, you must also trust the root user, as he can bypass file permissions and will be able to access your unencrypted private key file at any time.
Changing the private key's passphrase without changing the key
If the originally chosen SSH key passphrase is undesirable or must be changed, one can use the ssh-keygen command to change the passphrase without changing the actual key. This can also be used to change the password encoding format to the new standard.
Managing multiple keys
It is possible — although controversial [8][9] — to use the same SSH key pair for multiple hosts.
On the other hand, it is rather easy to maintain distinct keys for multiple hosts by using the IdentityFile directive in your openSSH config file:
See ssh_config(5) for full description of these options.
Storing SSH keys on hardware tokens
SSH keys can also be stored on a security token like a smart card or a USB token. This has the advantage that the private key is stored securely on the token instead of being stored on disk. When using a security token the sensitive private key is also never present in the RAM of the PC; the cryptographic operations are performed on the token itself. A cryptographic token has the additional advantage that it is not bound to a single computer; it can easily be removed from the computer and carried around to be used on other computers.
Examples are hardware tokens are described in:
- YubiKey#Using a YubiKey with SSH, and
Copying the public key to the remote server
This article or section needs expansion.
Once you have generated a key pair, you will need to copy the public key to the remote server so that it will use SSH key authentication. The public key file shares the same name as the private key except that it is appended with a .pub extension. Note that the private key is not shared and remains on the local machine.
Simple method
sh shell such as tcsh as default and uses OpenSSH older than 6.6.1p1. See this bug report.If your key file is ~/.ssh/id_rsa.pub you can simply enter the following command.
If your username differs on remote machine, be sure to prepend the username followed by @ to the server name.
If your public key filename is anything other than the default of ~/.ssh/id_rsa.pub you will get an error stating /usr/bin/ssh-copy-id: ERROR: No identities found. In this case, you must explicitly provide the location of the public key.
If the ssh server is listening on a port other than default of 22, be sure to include it within the host argument.
Manual method
By default, for OpenSSH, the public key needs to be concatenated with ~/.ssh/authorized_keys. Begin by copying the public key to the remote server.
The above example copies the public key (id_ecdsa.pub) to your home directory on the remote server via scp. Do not forget to include the : at the end of the server address. Also note that the name of your public key may differ from the example given.
On the remote server, you will need to create the ~/.ssh directory if it does not yet exist and append your public key to the authorized_keys file.
The last two commands remove the public key file from the server and set the permissions on the authorized_keys file such that it is only readable and writable by you, the owner.
SSH agents
If your private key is encrypted with a passphrase, this passphrase must be entered every time you attempt to connect to an SSH server using public-key authentication. Each individual invocation of ssh or scp will need the passphrase in order to decrypt your private key before authentication can proceed.
An SSH agent is a program which caches your decrypted private keys and provides them to SSH client programs on your behalf. In this arrangement, you must only provide your passphrase once, when adding your private key to the agent's cache. This facility can be of great convenience when making frequent SSH connections.
An agent is typically configured to run automatically upon login and persist for the duration of your login session. A variety of agents, front-ends, and configurations exist to achieve this effect. This section provides an overview of a number of different solutions which can be adapted to meet your specific needs.
ssh-agent
ssh-agent is the default agent included with OpenSSH. It can be used directly or serve as the back-end to a few of the front-end solutions mentioned later in this section. When ssh-agent is run, it forks to background and prints necessary environment variables. E.g.
To make use of these variables, run the command through the eval command.
Once ssh-agent is running, you will need to add your private key to its cache:
If your private key is encrypted, ssh-add will prompt you to enter your passphrase. Once your private key has been successfully added to the agent you will be able to make SSH connections without having to enter your passphrase.
ssh clients, including git store keys in the agent on first use, add the configuration setting AddKeysToAgent yes to ~/.ssh/config. Other possible values are confirm, ask and no (default).In order to start the agent automatically and make sure that only one ssh-agent process runs at a time, add the following to your ~/.bashrc:
This will run a ssh-agent process if there is not one already, and save the output thereof. If there is one running already, we retrieve the cached ssh-agent output and evaluate it which will set the necessary environment variables.
There also exist a number of front-ends to ssh-agent and alternative agents described later in this section which avoid this problem.
Start ssh-agent with systemd user
It is possible to use the systemd/User facilities to start the agent. Use this if you would like your ssh agent to run when you are logged in, regardless of whether x is running.
Add SSH_AUTH_SOCK DEFAULT='${XDG_RUNTIME_DIR}/ssh-agent.socket' to ~/.pam_environment. Then enable or start the service with the --user flag.
ssh-agent as a wrapper program
An alternative way to start ssh-agent (with, say, each X session) is described in this ssh-agent tutorial by UC Berkeley Labs. A basic use case is if you normally begin X with the startx command, you can instead prefix it with ssh-agent like so:
And so you do not even need to think about it you can put an alias in your .bash_aliases file or equivalent:
Doing it this way avoids the problem of having extraneous ssh-agent instances floating around between login sessions. Exactly one instance will live and die with the entire X session.
ssh-agent startx, you can add eval $(ssh-agent) to ~/.xinitrc.See the below notes on using x11-ssh-askpass with ssh-add for an idea on how to immediately add your key to the agent.
GnuPG Agent
The gpg-agent has OpenSSH agent emulation. See GnuPG#SSH agent for necessary configuration.
Keychain
Keychain is a program designed to help you easily manage your SSH keys with minimal user interaction. It is implemented as a shell script which drives both ssh-agent and ssh-add. A notable feature of Keychain is that it can maintain a single ssh-agent process across multiple login sessions. This means that you only need to enter your passphrase once each time your local machine is booted.
Installation
Install the keychain package.
Configuration
-Q, --quick option has the unexpected side-effect of making keychain switch to a newly-spawned ssh-agent upon relogin (at least on systems using GNOME), forcing you to re-add all the previously registered keys.Add a line similar to the following to your shell configuration file, e.g. if using Bash:
~/.bashrc is used instead of the upstream suggested ~/.bash_profile because on Arch it is sourced by both login and non-login shells, making it suitable for textual and graphical environments alike. See Bash#Invocation for more information on the difference between those.In the above example,
- the
--evalswitch outputs lines to be evaluated by the openingevalcommand; this sets the necessary environments variables for SSH client to be able to find your agent. --quietwill limit output to warnings, errors, and user prompts.
Multiple keys can be specified on the command line, as shown in the example. By default keychain will look for key pairs in the ~/.ssh/ directory, but absolute path can be used for keys in non-standard location. You may also use the --confhost option to inform keychain to look in ~/.ssh/config for IdentityFile settings defined for particular hosts, and use these paths to locate keys.
See keychain --help or keychain(1) for details on setting keychain for other shells.
To test Keychain, simply open a new terminal emulator or log out and back in your session. It should prompt you for the passphrase of the specified private key(s) (if applicable), either using the program set in $SSH_ASKPASS or on the terminal.
Because Keychain reuses the same ssh-agent process on successive logins, you should not have to enter your passphrase the next time you log in or open a new terminal. You will only be prompted for your passphrase once each time the machine is rebooted.
Tips
- keychain expects public key files to exist in the same directory as their private counterparts, with a
.pubextension. If the private key is a symlink, the public key can be found alongside the symlink or in the same directory as the symlink target (this capability requires thereadlinkcommand to be available on the system).
- to disable the graphical prompt and always enter your passphrase on the terminal, use the
--noguioption. This allows to copy-paste long passphrases from a password manager for example.
- if you do not want to be immediately prompted for unlocking the keys but rather wait until they are needed, use the
--noaskoption.
--agents option, e.g.--agents ssh,gpg. See keychain(1).x11-ssh-askpass
The x11-ssh-askpass package provides a graphical dialog for entering your passhrase when running an X session. x11-ssh-askpass depends only on the libx11 and libxt libraries, and the appearance of x11-ssh-askpass is customizable. While it can be invoked by the ssh-add program, which will then load your decrypted keys into ssh-agent, the following instructions will, instead, configure x11-ssh-askpass to be invoked by the aforementioned Keychain script.
Install the keychain and x11-ssh-askpass packages.
Edit your ~/.xinitrc file to include the following lines, replacing the name and location of your private key if necessary. Be sure to place these commands before the line which invokes your window manager.
In the above example, the first line invokes keychain and passes the name and location of your private key. If this is not the first time keychain was invoked, the following two lines load the contents of $HOSTNAME-sh and $HOSTNAME-sh-gpg, if they exist. These files store the environment variables of the previous instance of keychain.
Calling x11-ssh-askpass with ssh-add
The ssh-add manual page specifies that, in addition to needing the DISPLAY variable defined, you also need SSH_ASKPASS set to the name of your askpass program (in this case x11-ssh-askpass). It bears keeping in mind that the default Arch Linux installation places the x11-ssh-askpass binary in /usr/lib/ssh/, which will not be in most people's PATH. This is a little annoying, not only when declaring the SSH_ASKPASS variable, but also when theming. You have to specify the full path everywhere. Both inconveniences can be solved simultaneously by symlinking:
This is assuming that ~/bin is in your PATH. So now in your .xinitrc, before calling your window manager, one just needs to export the SSH_ASKPASS environment variable:
and your X resources will contain something like:
Doing it this way works well with the above method on using ssh-agent as a wrapper program. You start X with ssh-agent startx and then add ssh-add to your window manager's list of start-up programs.
Theming
The appearance of the x11-ssh-askpass dialog can be customized by setting its associated X resources. Some examples are the .ad files at https://github.com/sigmavirus24/x11-ssh-askpass. See x11-ssh-askpass(1)[dead link 2019-05-05] for full details.
Alternative passphrase dialogs
There are other passphrase dialog programs which can be used instead of x11-ssh-askpass. The following list provides some alternative solutions.
- ksshaskpass uses the KDE Wallet.
- openssh-askpass uses the Qt library.
pam_ssh
The pam_ssh project exists to provide a Pluggable Authentication Module (PAM) for SSH private keys. This module can provide single sign-on behavior for your SSH connections. On login, your SSH private key passphrase can be entered in place of, or in addition to, your traditional system password. Once you have been authenticated, the pam_ssh module spawns ssh-agent to store your decrypted private key for the duration of the session.

To enable single sign-on behavior at the tty login prompt, install the unofficial pam_sshAUR package.
~/.ssh/login-keys.d/.Create a symlink to your private key file and place it in ~/.ssh/login-keys.d/. Replace the id_rsa in the example below with the name of your own private key file.
Edit the /etc/pam.d/login configuration file to include the text highlighted in bold in the example below. The order in which these lines appear is significiant and can affect login behavior.
In the above example, login authentication initially proceeds as it normally would, with the user being prompted to enter his user password. The additional auth authentication rule added to the end of the authentication stack then instructs the pam_ssh module to try to decrypt any private keys found in the ~/.ssh/login-keys.d directory. The try_first_pass option is passed to the pam_ssh module, instructing it to first try to decrypt any SSH private keys using the previously entered user password. If the user's private key passphrase and user password are the same, this should succeed and the user will not be prompted to enter the same password twice. In the case where the user's private key passphrase user password differ, the pam_ssh module will prompt the user to enter the SSH passphrase after the user password has been entered. The optional control value ensures that users without an SSH private key are still able to log in. In this way, the use of pam_ssh will be transparent to users without an SSH private key.
If you use another means of logging in, such as an X11 display manager like SLiM or XDM and you would like it to provide similar functionality, you must edit its associated PAM configuration file in a similar fashion. Packages providing support for PAM typically place a default configuration file in the /etc/pam.d/ directory.
Further details on how to use pam_ssh and a list of its options can be found in the pam_ssh(8) man page.
Using a different password to unlock the SSH key
If you want to unlock the SSH keys or not depending on whether you use your key's passphrase or the (different!) login password, you can modify /etc/pam.d/system-auth to
For an explanation, see [10].
Known issues with pam_ssh
Work on the pam_ssh project is infrequent and the documentation provided is sparse. You should be aware of some of its limitations which are not mentioned in the package itself.
- Versions of pam_ssh prior to version 2.0 do not support SSH keys employing the newer option of ECDSA (elliptic curve) cryptography. If you are using earlier versions of pam_ssh you must use either RSA or DSA keys.
- The
ssh-agentprocess spawned by pam_ssh does not persist between user logins. If you like to keep a GNU Screen session active between logins you may notice when reattaching to your screen session that it can no longer communicate with ssh-agent. This is because the GNU Screen environment and those of its children will still reference the instance of ssh-agent which existed when GNU Screen was invoked but was subsequently killed in a previous logout. The Keychain front-end avoids this problem by keeping the ssh-agent process alive between logins.
pam_exec-ssh
As an alternative to pam_ssh you can use pam_exec-sshAUR. It is a shell script that uses pam_exec. Help for configuration can be found upstream.
GNOME Keyring
If you use the GNOME desktop, the GNOME Keyring tool can be used as an SSH agent. See the GNOME Keyring article for further details.
Store SSH keys with Kwallet
For instructions on how to use kwallet to store your SSH keys, see KDE Wallet#Using the KDE Wallet to store ssh key passphrases.
KeePass2 with KeeAgent plugin
KeeAgent is a plugin for KeePass that allows SSH keys stored in a KeePass database to be used for SSH authentication by other programs.
- Supports both PuTTY and OpenSSH private key formats.
- Works with native SSH agent on Linux/Mac and with PuTTY on Windows.
See KeePass#Plugin Installation in KeePass or install the keepass-plugin-keeagent package.
This agent can be used directly, by matching KeeAgent socket: KeePass -> Tools -> Options -> KeeAgent -> Agent mode socket file -> %XDG_RUNTIME_DIR%/keeagent.socket-and environment variable:export SSH_AUTH_SOCK='$XDG_RUNTIME_DIR'/keeagent.socket'.
KeePassXC
The KeePassXC fork of KeePass supports being used as an SSH agent by default. It is also compatible with KeeAgent's database format.
Troubleshooting
Key ignored by the server
- If it appears that the SSH server is ignoring your keys, ensure that you have the proper permissions set on all relevant files.
- For the local machine:
- For the remote machine:
- If that does not solve the problem you may try temporarily setting
StrictModestonoin/etc/ssh/sshd_config. If authentication withStrictModes offis successful, it is likely an issue with file permissions persists.
- Make sure keys in
~/.ssh/authorized_keysare entered correctly and only use one single line. - Make sure the remote machine supports the type of keys you are using: some servers do not support ECDSA keys, try using RSA or DSA keys instead, see #Generating an SSH key pair.
- You may want to use debug mode and monitor the output while connecting:
See also
- OpenSSH key management: Part 1, Part 2, Part 3
How to Generate a Public/Private KeyPair for Use With Solaris Secure Shell
Users must generate a public/private key pair when their site implementshost-based authentication or user public-key authentication. For additionaloptions, see the ssh-keygen(1) manpage.
Before You Begin
Determine from your system administrator if host-based authenticationis configured.
Start the key generation program.
where -t is the type of algorithm, one of rsa, dsa, or rsa1.
Specify the path to the file that will hold the key.
Bydefault, the file name id_rsa, which represents an RSAv2 key, appears in parentheses. You can select this file by pressing the Return key. Or, you can type an alternative file name.
The file name of the public key is created automatically by appendingthe string .pub to the name of the private key file.
Type a passphrase for using your key.
This passphraseis used for encrypting your private key. A null entry is stronglydiscouraged. Note that the passphrase is not displayed when youtype it in.
Retype the passphrase to confirm it.
Check the results.
Check that the path to the keyfile is correct.
At this point, you have created a public/private key pair.
Choose the appropriate option:
If your administrator has configuredhost-based authentication, you might need to copy the local host's publickey to the remote host.
You can now log in to the remote host.For details, see How to Log In to a Remote Host With Solaris Secure Shell.
Type the command on one line with no backslash.
When you are prompted, supply your login password.
If your site uses user authentication with public keys, populateyour authorized_keys file on the remote host.
Copy your public key to the remote host.
Type thecommand on one line with no backslash.
When you are prompted, supply your login password.
Whenthe file is copied, the message “Key copied” is displayed.
(Optional) Reduce the prompting for passphrases.
For a procedure, see How to Reduce Password Prompts in Solaris Secure Shell. For more information, see the ssh-agent(1) and ssh-add(1) man pages.
Example 19–2 Establishing a v1 RSA Key for a User
In the following example, the user cancontact hosts that run v1 of the Solaris Secure Shell protocol. To be authenticated by v1hosts, the user creates a v1 key, then copies the public key portion to theremote host.

Microsoft Visual Studio Express 2012 Product Key Generator

Microsoft Visual Studio Product Key. Microsoft Visual Studio All Editions Product Key: Visual Studio Serial Key provides the most comprehensive solution to easily deliver applications across all Microsoft platforms, including phone, desktop, tablet, server, and the cloud. With an included MSDN subscription, you get access to thousands of Microsoft products and additional services—so you. I have been using VS Express 2012 for almost a month and now it states that I must enter a product key to continue using it. To get that product key I am asked to register. Only after creating a Microsoft account (great, another account to keep track of) does it inform me that I must enter details about my company, its address, its employees. Our company need a license and key for Visual Studio 2012 to be able to edit forms we’ve previously created with InfoPath. (Later versions of Visual Studio are incompatible.) Our Microsoft account manager sold us Visual Studio Professional with MSDN which comes with Software Assurance.
- Microsoft Visual Studio Express 2012 Product Key Generator Price
- Visual Studio Express
- Download Visual Studio Express 2012
È possibile applicare il codice Product Key a livello di programmazione come parte dello script utilizzato per automatizzare la distribuzione di Visual Studio.You can apply your product key programmatically as part of a script that is used to automate the deployment of Visual Studio.È possibile impostare i codici Product Key su un dispositivo a livello di programmazione durante l'installazione di Visual Studio o al termine dell'installazione.You can set a product key on a device programmatically either during an installation of Visual Studio or after an installation completes.
Applicare la licenza dopo l'installazioneApply the license after installation
È possibile attivare una versione installata di Visual Studio con un codice Product Key tramite l'utilità StorePID.exe nei computer di destinazione in modalità invisibile all'utente.You can activate an installed version of Visual Studio with a product key by using the StorePID.exe utility on the target machines, in silent mode.StorePID.exe è un programma di utilità che viene installato con Visual Studio 2017 nel percorso predefinito seguente:StorePID.exe is a utility program that installs with Visual Studio 2017 at the following default location:C:Program Files (x86)Microsoft Visual Studio2017EnterpriseCommon7IDE
È possibile attivare una versione installata di Visual Studio con un codice Product Key tramite l'utilità StorePID.exe nei computer di destinazione in modalità invisibile all'utente.You can activate an installed version of Visual Studio with a product key by using the StorePID.exe utility on the target machines, in silent mode.StorePID.exe è un programma di utilità che viene installato con Visual Studio 2019 nel percorso predefinito seguente:StorePID.exe is a utility program that installs with Visual Studio 2019 at the following default location:C:Program Files (x86)Microsoft Visual Studio2019EnterpriseCommon7IDE
Eseguire StorePID.exe con privilegi elevati, usando un agente System Center o un prompt dei comandi con privilegi elevati.Run StorePID.exe with elevated privileges, either by using a System Center agent or an elevated command prompt.Continuare quindi con il codice Product Key (con i trattini) e il codice Microsoft Product Code (MPC).Follow it with the product key and the Microsoft Product Code (MPC).
Importante
Assicurarsi di includere i trattini nel codice Product Key.Make sure to include the dashes in the product key.

In questo esempio è riportata una riga di comando per l'applicazione della licenza di Visual Studio 2017 Enterprise, con codice MPC 08860 e codice Product Key AAAAA-BBBBB-CCCCC-DDDDDD-EEEEEE, presupponendone l'installazione in un percorso predefinito:The following example shows a command line for applying the license for Visual Studio 2017 Enterprise, which has an MPC of 08860, a product key of AAAAA-BBBBB-CCCCC-DDDDDD-EEEEEE, and assumes a default installation location:
In questo esempio è riportata una riga di comando per l'applicazione della licenza di Visual Studio 2019 Enterprise, con codice MPC 09260 e codice Product Key AAAAA-BBBBB-CCCCC-DDDDDD-EEEEEE, presupponendone l'installazione nel percorso predefinito:The following example shows a command line for applying the license for Visual Studio 2019 Enterprise, which has an MPC of 09260, a product key of AAAAA-BBBBB-CCCCC-DDDDDD-EEEEEE, and assumes a default installation location:
La tabella seguente riporta i codici MPC per ogni edizione di Visual Studio:The following table lists the MPC codes for each edition of Visual Studio:
| Edizione di Visual StudioVisual Studio Edition | MPCMPC |
|---|---|
| Visual Studio Enterprise 2017Visual Studio Enterprise 2017 | 0886008860 |
| Visual Studio Professional 2017Visual Studio Professional 2017 | 0886208862 |
| Visual Studio Test Professional 2017Visual Studio Test Professional 2017 | 0886608866 |
| Edizione di Visual StudioVisual Studio Edition | MPCMPC |
|---|---|
| Visual Studio Enterprise 2019Visual Studio Enterprise 2019 | 0926009260 |
| Visual Studio Professional 2019Visual Studio Professional 2019 | 0926209262 |
Se StorePID.exe applica correttamente il codice Product Key, restituisce un %ERRORLEVEL% pari a 0.If StorePID.exe successfully applies the product key, it returns an %ERRORLEVEL% of 0.Se si verificano errori, verrà restituito uno dei codici seguenti, a seconda della condizione di errore:If it encounters errors, it returns one of the following codes, depending on the error condition:
| ErroreError | CodiceCode |
|---|---|
PID_ACTION_SUCCESS | 00 |
PID_ACTION_NOTINSTALLED | 11 |
PID_ACTION_INVALID | 22 |
PID_ACTION_EXPIRED | 33 |
PID_ACTION_INUSE | 44 |
PID_ACTION_FAILURE | 55 |
PID_ACTION_NOUPGRADE | 66 |
Nota
Quando si esegue un'istanza virtuale di Visual Studio, assicurarsi di virtualizzare anche la cartella AppData locale e il Registro di sistema.When you run a virtual instance of Visual Studio, make sure that you also virtualize the local AppData folder and the registry.Per risolvere i C:Program Files (x86)Microsoft Visual Studio<version>Common7IDEDDConfigCA.exeproblemi relativi alle istanze virtuali, eseguire .To troubleshoot virtual instances, run C:Program Files (x86)Microsoft Visual Studio<version>Common7IDEDDConfigCA.exe.
SupportoGet support
Non sempre tutto funziona correttamente.Sometimes, things can go wrong.Se l'installazione di Visual Studio non riesce, vedere Risolvere i problemi di installazione e aggiornamento di Visual Studio per istruzioni dettagliate.If your Visual Studio installation fails, see Troubleshoot Visual Studio installation and upgrade issues for step-by-step guidance.
Per i problemi correlati all'installazione è disponibile anche un'opzione di supporto che offre una chat per l'installazione (solo in lingua inglese).We also offer an installation chat (English only) support option for installation-related issues.
Ecco alcune altre opzioni di supporto:Here are a few more support options:
- Segnalare i problemi del prodotto a Microsoft tramite lo strumento Segnala un problema che viene visualizzato sia nel programma di installazione di Visual Studio che nell'IDE di Visual Studio.Report product issues to us via the Report a Problem tool that appears both in the Visual Studio Installer and in the Visual Studio IDE.
- Suggerire una funzionalità, tenere traccia dei problemi del prodotto e trovare risposte in Visual Studio Developer Community.Suggest a feature, track product issues, and find answers in the Visual Studio Developer Community.
- Usare l'account GitHub per comunicare con gli sviluppatori Microsoft e altri sviluppatori di Visual Studio partecipando alla conversazione dedicata a Visual Studio nella community di Gitter.Use your GitHub account to talk to us and other Visual Studio developers in the Visual Studio conversation in the Gitter community.
Vedere ancheSee also
Microsoft Visual Studio Express 2012 Product Key Generator Price
-->If you want to publish an application by using ClickOnce deployment, the application and deployment manifests must be signed with a public/private key pair and signed using Authenticode technology. You can sign the manifests by using a certificate from the Windows certificate store or a key file.
For more information about ClickOnce deployment, see ClickOnce security and deployment.
Signing the ClickOnce manifests is optional for .exe-based applications. For more information, see the 'Generate unsigned manifests' section of this document.
For information about creating key files, see How to: Create a public-private key pair.
Note
Visual Studio supports only Personal Information Exchange (PFX) key files that have the .pfx extension. However, you can select other types of certificates from the current user's Windows certificate store by clicking Select from Store on the Signing page of project properties.
Sign using a certificate
Go to the project properties window (right-click the project node in Solution Explorer and select Properties). On the Signing tab, select the Sign the ClickOnce manifests check box.
Click the Select from Store button.
The Select a Certificate dialog box appears and displays the contents of the Windows certificate store.
Tip
If you click Click here to view certificate properties, the Certificate Details dialog box appears. This dialog box includes detailed information about the certificate and additional options. Click Certificates to view additional help information.
Select the certificate that you want to use to sign the manifests.
Additionally, you can specify the address of a timestamp server in the Timestamp server URL text box. This is a server that provides a timestamp specifying when the manifest was signed.
Sign using an existing key file
On the Signing page, select the Sign the ClickOnce manifests check box.
Click the Select from File button.
The Select File dialog box appears.
In the Select File dialog box, browse to the location of the key file (.pfx) that you want to use, and then click Open.
Note
This option supports only files that have the .pfx extension. If you have a key file or certificate in another format, store it in the Windows certificate store and select the certificate is described in the previous procedure. The selected certificate's purpose should include code signing.
The Enter password to open file dialog box appears. (If the .pfx file is already stored in your Windows certificate store or is not password protected, you aren't prompted to enter a password.)
Enter the password to access the key file, and then select Enter.
Note
The .pfx file cannot include certificate chaining information. If it does, the following import error will occur: Cannot find the certificate and private key for decryption. To remove the certificate chaining information, you can use Certmgr.msc and disable the option to Include all certificates when exporting the *.pfx file.
Sign using a test certificate
On the Signing page, select the Sign the ClickOnce manifests check box.
To create a new certificate for testing, click the Create Test Certificate button.
In the Create Test Certificate dialog box, enter a password to help secure your test certificate.
Generate unsigned manifests
Signing the ClickOnce manifests is optional for .exe-based applications. The following procedures show how to generate unsigned ClickOnce manifests.
Important
Unsigned manifests can simplify development and testing of your application. However, unsigned manifests introduce substantial security risks in a production environment. Only consider using unsigned manifests if your ClickOnce application runs on computers within an intranet that is completely isolated from the internet or other sources of malicious code.
By default, ClickOnce automatically generates signed manifests unless one or more files are specifically excluded from the generated hash. In other words, publishing the application results in signed manifests if all files are included in the hash, even when the Sign the ClickOnce manifests check box is cleared.
To generate unsigned manifests and include all files in the generated hash
To generate unsigned manifests that include all files in the hash, you must first publish the application together with signed manifests. Therefore, first sign the ClickOnce manifests by following one of the previous procedures, and then publish the application.
On the Signing page, clear the Sign the ClickOnce manifests check box.
Reset the publish version so that only one version of your application is available. By default, Visual Studio automatically increments the revision number of the publish version every time that you publish an application. For more information, see How to: Set the ClickOnce publish version.
Publish the application.
To generate unsigned manifests and exclude one or more files from the generated hash
Visual Studio Express
On the Signing page, clear the Sign the ClickOnce manifests check box.
Open the Application Files dialog box and set the Hash to Exclude for the files that you want to exclude from the generated hash.
Note
Excluding a file from the hash configures ClickOnce to disable automatic signing of the manifests, so you do not need to first publish with signed manifests as shown in the previous procedure.
Publish the application.
Download Visual Studio Express 2012
See also

Before You Generate The Rsa Key You Must

After you’ve generated an API signing key, you must upload the public key for the associated user in Oracle Cloud Infrastructure. The first time you upload an API signing key, you must use the Console. Subsequently, you can also use the API to upload an API key. Sign in to the Oracle Cloud Infrastructure Console. Click Identity and then click Users. Before adding a new SSH key to the ssh-agent to manage your keys, you should have checked for existing SSH keys and generated a new SSH key. When adding your SSH key to the agent, use the default macOS ssh-add command, and not an application installed by macports, homebrew, or some other external source. Mar 03, 2020 Generating an RSA key with a self-signed X.509 certificate If you're validating keys against registry-level certificates, the certificate must meet. Oct 05, 2007 Generating public keys for authentication is the basic and most often used feature of ssh-keygen. Ssh-keygen can generate both RSA and DSA keys. RSA keys have a minimum key length of 768 bits and the default length is 2048. When generating new RSA keys you should use at least 2048 bits of key length unless you really have a good reason for.
- October 2, 2015
- Posted by: Syed Shujaat
- Category: Cisco, Networking Solutions
Use this command to generate RSA key pairs for your Cisco device (such as a router). keys are generated in pairs–one public RSA key and one private RSA key.
If your router already has RSA keys when you issue this command, you will be warned and prompted to replace the existing keys with new keys.
NOTE: Before issuing this command, ensure that your router has a hostname and IP domain name configured (with the hostname and ipdomain-name commands).
You will be unable to complete the cryptokeygeneratersacommand without a hostname and IP domain name. (This situation is not true when you generate only a named key pair.)
Here are the steps to Enable SSH and Crypto Key setup : 2 config must requried for SSH
1 Setup Local VTY line User ID and password
router (Config) # Line VTY 0 15
router (Config-line)# login local
router (Config-line)# Exit
!!! create local login ID/Pass
router (Config)# username [loginid] password [cisco]
router (Config)# username loginid1 password cisco1
2. router (Config)# ip domain-name example.com
Rsa Key Generation Program
router (Config)# crypto key generate rsa
how many bits in the modulus [512] :1024
router (Config)# ip ssh version2
router (Config)# CTRL Z
Note | Secure Shell (SSH) may generate an additional RSA key pair if you generate a key pair on a router having no RSA keys. The additional key pair is used only by SSH and will have a name such as {router_FQDN }.server. For example, if a router name is “router1.cisco.com,” the key name is “router1.cisco.com.server.” |
This command is not saved in the router configuration; however, the RSA keys generated by this command are saved in the private configuration in NVRAM (which is never displayed to the user or backed up to another device) the next time the configuration is written to NVRAM.
Modulus Length
When you generate RSA keys, you will be prompted to enter a modulus length. The longer the modulus, the stronger the security. However, a longer modules take longer to generate (see the table below for sample times) and takes longer to use.
The size of Key Modulus range from 360 to 2048. Choosing modulus greater than 512 will take longer time.
| Router | 360 bits | 512 bits | 1024 bits | 2048 bits (maximum) |
|---|---|---|---|---|
| Cisco 2500 | 11 seconds | 20 seconds | 4 minutes, 38 seconds | More than 1 hour |
| Cisco 4700 | Less than 1 second | 1 second | 4 seconds | 50 seconds |
Cisco IOS software does not support a modulus greater than 4096 bits. A length of less than 512 bits is normally not recommended. In certain situations, the shorter modulus may not function properly with IKE, so we recommend using a minimum modulus of 2048 bits.
Syntax Description : Optional Strings to embed with SSH Crypto key
| general-keys | (Optional) Specifies that a general-purpose key pair will be generated, which is the default. | ||
| usage-keys | (Optional) Specifies that two RSA special-usage key pairs, one encryption pair and one signature pair, will be generated. | ||
| signature | (Optional) Specifies that the RSA public key generated will be a signature special usage key. | ||
| encryption | (Optional) Specifies that the RSA public key generated will be an encryption special usage key. | ||
| labelkey-label | (Optional) Specifies the name that is used for an RSA key pair when they are being exported.If a key label is not specified, the fully qualified domain name (FQDN) of the router is used. | ||
| exportable | (Optional) Specifies that the RSA key pair can be exported to another Cisco device, such as a router. | ||
| modulusmodulus-size | (Optional) Specifies the IP size of the key modulus.By default, the modulus of a certification authority (CA) key is 1024 bits. The recommended modulus for a CA key is 2048 bits. The range of a CA key modulus is from 350 to 4096 bits.
| ||
| storagedevicename: | (Optional) Specifies the key storage location. The name of the storage device is followed by a colon (:). | ||
| redundancy | (Optional) Specifies that the key should be synchronized to the standby CA. | ||
| ondevicename: | (Optional) Specifies that the RSA key pair will be created on the specified device, including a Universal Serial Bus (USB) token, local disk, or NVRAM. The name of the device is followed by a colon (:).Keys created on a USB token must be 2048 bits or less. |
| Command | Description |
|---|---|
| copy | Copies any file from a source to a destination, use the copy command in privileged EXEC mode. |
| cryptokeystorage | Sets the default storage location for RSA key pairs. |
| debugcryptoengine | Displays debug messages about crypto engines. |
| hostname | Specifies or modifies the hostname for the network server. |
| ipdomain-name | Defines a default domain name to complete unqualified hostnames (names without a dotted-decimal domain name). |
| showcryptokeymypubkeyrsa | Displays the RSA public keys of your router. |
| show crypto pki certificates | Displays information about your PKI certificate, certification authority, and any registration authority certificates. |
-->
With a secure shell (SSH) key pair, you can create virtual machines (VMs) in Azure that use SSH keys for authentication, eliminating the need for passwords to sign in. This article shows you how to quickly generate and use an SSH public-private key file pair for Linux VMs. You can complete these steps with the Azure Cloud Shell, a macOS or Linux host, the Windows Subsystem for Linux, and other tools that support OpenSSH.
Note
VMs created using SSH keys are by default configured with passwords disabled, which greatly increases the difficulty of brute-force guessing attacks.
For more background and examples, see Detailed steps to create SSH key pairs.
For additional ways to generate and use SSH keys on a Windows computer, see How to use SSH keys with Windows on Azure.

Supported SSH key formats
Azure currently supports SSH protocol 2 (SSH-2) RSA public-private key pairs with a minimum length of 2048 bits. Other key formats such as ED25519 and ECDSA are not supported.
Create an SSH key pair
Use the ssh-keygen command to generate SSH public and private key files. By default, these files are created in the ~/.ssh directory. You can specify a different location, and an optional password (passphrase) to access the private key file. If an SSH key pair with the same name exists in the given location, those files are overwritten.
The following command creates an SSH key pair using RSA encryption and a bit length of 4096:
If you use the Azure CLI to create your VM with the az vm create command, you can optionally generate SSH public and private key files using the --generate-ssh-keys option. The key files are stored in the ~/.ssh directory unless specified otherwise with the --ssh-dest-key-path option. The --generate-ssh-keys option will not overwrite existing key files, instead returning an error. In the following command, replace VMname and RGname with your own values:
Provide an SSH public key when deploying a VM
To create a Linux VM that uses SSH keys for authentication, specify your SSH public key when creating the VM using the Azure portal, Azure CLI, Azure Resource Manager templates, or other methods:
If you're not familiar with the format of an SSH public key, you can display your public key with the following cat command, replacing ~/.ssh/id_rsa.pub with the path and filename of your own public key file if needed:
A typical public key value looks like this example:
If you copy and paste the contents of the public key file to use in the Azure portal or a Resource Manager template, make sure you don't copy any trailing whitespace. To copy a public key in macOS, you can pipe the public key file to pbcopy. Similarly in Linux, you can pipe the public key file to programs such as xclip.
Before You Generate The Rsa Key You Must Take
The public key that you place on your Linux VM in Azure is by default stored in ~/.ssh/id_rsa.pub, unless you specified a different location when you created the key pair. To use the Azure CLI 2.0 to create your VM with an existing public key, specify the value and optionally the location of this public key using the az vm create command with the --ssh-key-values option. In the following command, replace VMname, RGname, and keyFile with your own values:
If you want to use multiple SSH keys with your VM, you can enter them in a space-separated list, like this --ssh-key-values sshkey-desktop.pub sshkey-laptop.pub.
SSH into your VM
With the public key deployed on your Azure VM, and the private key on your local system, SSH into your VM using the IP address or DNS name of your VM. In the following command, replace azureuser and myvm.westus.cloudapp.azure.com with the administrator user name and the fully qualified domain name (or IP address):
If you specified a passphrase when you created your key pair, enter that passphrase when prompted during the login process. The VM is added to your ~/.ssh/known_hosts file, and you won't be asked to connect again until either the public key on your Azure VM changes or the server name is removed from ~/.ssh/known_hosts.
If the VM is using the just-in-time access policy, you need to request access before you can connect to the VM. For more information about the just-in-time policy, see Manage virtual machine access using the just in time policy.
Next steps
For more information on working with SSH key pairs, see Detailed steps to create and manage SSH key pairs.
If you have difficulties with SSH connections to Azure VMs, see Troubleshoot SSH connections to an Azure Linux VM.

Openssl Key Generation Without Password

The openssl program provides a rich variety of commands, each of which often has a wealth of options and arguments. Many commands use an external configuration file for some or all of their arguments and have a -config option to specify that file. The environment variable OPENSSL_CONF can be used to specify the location of the configuration file. If the environment variable is not specified, a default file is created in the default certificate storage area called openssl.cnf. The settings in this default configuration file depend on the flags set when the version of OpenSSL being used was built.
- Openssl Key Password
- Openssl Key Generation Without Password Download
- Openssl Genrsa No Password
- Openssl Key Generation Without Password Key
Generate an RSA private key using default parameters: openssl genpkey -algorithm RSA -out key.pem. Encrypt output private key using 128 bit AES and the passphrase 'hello': openssl genpkey -algorithm RSA -out key.pem -aes-128-cbc -pass pass:hello. Generate a 2048 bit RSA key using 3 as the public exponent. Add -pass file:nameofkeyfile to the OpenSSL command line. This causes OpenSSL to read the password/passphrase from the named file, but otherwise proceed normally. For more details, see the man page for openssl(1) (man 1 openssl) and particularly its section 'PASS PHRASE ARGUMENTS', and the man page for enc(1) (man 1 enc).If the key file actually holds the encryption key (not something.
This article is an overview of the available tools provided by openssl. For all of the details on usage and implementation, you can find the manpages which are automatically generated from the source code at the official OpenSSL project home. Likewise, the source code itself may be found on the OpenSSL project home page, as well as on the OpenSSL Github. The main OpenSSL site also includes an overview of the command-line utilities, as well as links to all of their respective documentation.
- 2Basic Tasks
- 2.5Generating Keys Based on Elliptic Curves
- 2.5.1Generating the Curve Parameters
- 2.5Generating Keys Based on Elliptic Curves
- 3Commands
The entry point for the OpenSSL library is the openssl binary, usually /usr/bin/openssl on Linux. The general syntax for calling openssl is as follows:
Alternatively, you can call openssl without arguments to enter the interactive mode prompt. You may then enter commands directly, exiting with either a quit command or by issuing a termination signal with either Ctrl+C or Ctrl+D. The following is a sample interactive session in which the user invokes the prime command twice before using the quit command to terminate the session.
This section is a brief tutorial on performing the most basic tasks using OpenSSL. For a detailed explanation of the rationale behind the syntax and semantics of the commands shown here, see the section on Commands.
Getting Help[edit]
As mentioned previously, the general syntax of a command is openssl command [ command_options ] [ command_arguments ]. The help command is no different, but it does have its idiosyncrasies. To view the top-level help menu, you can call openssl as follows.
This query will print all of the available commands, like so:
Note the above output was truncated, so only the first four lines of output are shown.
A help menu for each command may be requested in two different ways. First, the same command used above may be repeated, followed by the name of the command to print help for.
The program will then display the valid options for the given command.
The second way of requesting the help menu for a particular command is by using the first option in the output shown above, namely openssl command -help. Both commands will yield the same output; the help menu displayed will be exactly the same.
For additional information on the usage of a particular command, the project manpages are a great source of information. Another excellent source of information is the project perldocs. perldoc is a utility included with most if not all Perl distributions, and it's capable of displaying documentation information in a variety of formats, one of which is as manpages. Not surprisingly, the project documentation is generated from the pod files located in the doc directory of the source code.
Getting Library Version Information[edit]
As mentioned above, the version command's help menu may be queried for additional options like so:
Using the -a option to show all version information yields the following output on my current machine:
Generating an RSA Private Key[edit]
Generating a private key can be done in a variety of different ways depending on the type of key, algorithm, bits, and other options your specific use case may require. In this example, we are generating a private key using RSA and a key size of 2048 bits.
To generate a password protected private key, the previous command may be slightly amended as follows:
The addition of the -aes256 option specifies the cipher to use to encrypt the private key file. For a list of available ciphers in the library, you can run the following command:
With your private key in hand, you can use the following command to see the key's details, such as its modulus and its constituent primes. Remember to change the name of the input file to the file name of your private key.
The above command yields the following output in my specific case. Your output will differ but should be structurally similar.
Keep in mind the above key was generated solely for pedagogical purposes; never give anyone access to your private keys.
Generating a Public Key[edit]
Having previously generated your private key, you may generate the corresponding public key using the following command.
You may once again view the key details, using a slightly different command this time.
The output for the public key will be shorter, as it carries much less information, and it will look something like this.
For more information on generating keys, see the source code documentation, located in the doc/HOWTO/keys.txt file.
Generating Keys Based on Elliptic Curves[edit]
There are essentially two steps to generating a key:
- Generate the parameters for the specific curve you are using
- Use those parameters to generate the key
To see the list of curves instrinsically supported by openssl, you can use the -list_curves</t> option when calling the <tt>ecparam command.
For this example I will use the prime256v1 curve, which is an X9.62/SECG curve over a 256 bit prime field.
Generating the Curve Parameters[edit]
Having selected our curve, we now call ecparam to generate our parameters file.
Printing Parameters to Standard Out[edit]
You can print the generated curve parameters to the terminal output with the following command:
Printing Parameters as C Code[edit]
Analogously, you may also output the generated curve parameters as C code. The parameters can then be loaded by calling the get_ec_group_XXX() function. To print the C code to the current terminal's output, the following command may be used:
And here are the first few lines of the corresponding output:
Generating the Key[edit]
With the curve parameters in hand, we are now free to generate the key. Just as with the [#Generating an RSA Private Key|RSA] example above, we may optionally specify a cipher algorithm with which to encrypt the private key. The call to generate the key using the elliptic curve parameters generated in the example above looks like this:
Putting it All Together[edit]
The process of generation a curve based on elliptic-curves can be streamlined by calling the genpkey command directly and specifying both the algorithm and the name of the curve to use for parameter generation. In it's simplest form, the command to generate a key based on the same curve as in the example above looks like this:
This command will result in the generated key being printed to the terminal's output.
Remember that you can specify a cipher algorithm to encrypt the key with, which something you may or may not want to do, depending on your specific use case. Here is a slightly more complete example showing a key generated with a password and written to a specific output file.
Just as with the previous example, you can use the pkey command to inspect your newly-generated key.
For more details on elliptic curve cryptography or key generation, check out the manpages.
Base64 Encoding Strings[edit]
Openssl Key Password
For simple string encoding, you can use 'here string' syntax with the base64 command as below. Intuitively, the -e flag specifies the action to be encoding.
Similarly, the base64 command's -d flag may be used to indicate decoding mode.
Generating a File Hash[edit]
One of the most basic uses of the dgst command (short for digest) is viewing the hash of a given file. To do this, simply invoke the command with the specified digest algorithm to use. For this example, I will be hashing an arbitrary file on my system using the MD5, SHA1, and SHA384 algorithms.
For a list of the available digest algorithms, you can use the following command.
You can also use a similar command to see the available digest commands:
Below are three sample invocations of the md5, sha1, and sha384 digest commands using the same file as the dgst command invocation above.
File Encryption and Decryption[edit]
The following example demonstrates a simple file encryption and decryption using the enc command. The first argument is the cipher algorithm to use for encrypting the file. For this example I carefully selected the AES-256 algorithm in CBC Mode by looking up the available ciphers and picking out the first one I saw. To see the list of available ciphers, you can use the following command.
You can also use the following command:
Having selected an encryption algorithm, you must then specify whether the action you are taking is either encryption or decryption via the -e or -d flags, respectively. The -iter flag specifies the number of iterations on the password used for deriving the encryption key. A higher iteration count increases the time required to brute-force the resulting file. Using this option implies enabling use of the Password-Based Key Derivation Function 2, usually set using the -pbkdf2 flag. We then use the -salt flag to enable the use of a randomly generated salt in the key-derivation function.
Putting it all together, you can see the command to encrypt a file and the corresponding output below. Note that the passwords entered by the user are blank, just as they would usually be in a terminal session.
Openssl Key Generation Without Password Download
The analogous decryption command is as follows:
There are three different kinds of commands. These are standard commands, cipher commands, and digest commands. Calling the OpenSSL top-level help command with no arguments will result in openssl printing all available commands by group, sorted alphabetically.
Standard Commands[edit]
| Command | Description |
|---|---|
| asn1parse | Parse an ASN.1 sequence. |
| ca | Certificate Authority (CA) Management. |
| ciphers | Cipher Suite Description Determination. |
| cms | CMS (Cryptographic Message Syntax) utility. |
| crl | Certificate Revocation List (CRL) Management. |
| crl2pkcs7 | CRL to PKCS#7 Conversion. |
| dgst | Message Digest calculation. MAC calculations are superseded by mac(1). |
| dhparam | Generation and Management of Diffie-Hellman Parameters. Superseded by genpkey(1) and pkeyparam(1). |
| dsa | DSA Data Management. |
| dsaparam | DSA Parameter Generation and Management. Superseded by genpkey(1) and pkeyparam(1). |
| ec | EC (Elliptic curve) key processing. |
| ecparam | EC parameter manipulation and generation. |
| enc | Encoding with Ciphers. |
| engine | Engine (loadable module) information and manipulation. |
| errstr | Error Number to Error String Conversion. |
| gendsa | Generation of DSA Private Key from Parameters. Superseded by genpkey(1) and pkey(1). |
| genpkey | Generation of Private Key or Parameters. |
| genrsa | Generation of RSA Private Key. Superseded by genpkey(1). |
| info | Display diverse information built into the OpenSSL libraries. |
| kdf | Key Derivation Functions. |
| mac | Message Authentication Code Calculation. |
| nseq | Create or examine a Netscape certificate sequence. |
| ocsp | Online Certificate Status Protocol utility. |
| passwd | Generation of hashed passwords. |
| pkcs12 | PKCS#12 Data Management. |
| pkcs7 | PKCS#7 Data Management. |
| pkcs8 | PKCS#8 format private key conversion tool. |
| pkey | Public and private key management. |
| pkeyparam | Public key algorithm parameter management. |
| pkeyutl | Public key algorithm cryptographic operation utility. |
| prime | Compute prime numbers. |
| rand | Generate pseudo-random bytes. |
| rehash | Create symbolic links to certificate and CRL files named by the hash values. |
| req | PKCS#10 X.509 Certificate Signing Request (CSR) Management. |
| rsa | RSA key management. |
| rsautl | RSA utility for signing, verification, encryption, and decryption. Superseded by pkeyutl(1). |
| s_client | This implements a generic SSL/TLS client which can establish a transparent connection to a remote server speaking SSL/TLS. |
| s_server | This implements a generic SSL/TLS server which accepts connections from remote clients speaking SSL/TLS. |
| s_time | SSL Connection Timer. |
| sess_id | SSL Session Data Management. |
| smime | S/MIME mail processing. |
| speed | Algorithm Speed Measurement. |
| spkac | SPKAC printing and generating utility. |
| srp | Maintain SRP password file. |
| storeutl | Utility to list and display certificates, keys, CRLs, etc. |
| ts | Time Stamping Authority tool (client/server). |
| verify | X.509 Certificate Verification. |
| version | OpenSSL Version Information. |
| x509 | X.509 Certificate Data Management. |
Openssl Genrsa No Password
- Paul Heinlein. 'OpenSSL Command-Line HOWTO'. Has many quick cookbook-style recipes for doing common tasks using the 'oppenssl' command-line application.
Openssl Key Generation Without Password Key

Generate Pem From Key Crt

- Jul 17, 2017 How to Generate pem file to ssh the server without Password in Linux. The main file extensions are.pem,.crt. To generate an RSA key pair for version 2 of.
- .crt stands simply for certificate, usually an X509v3 certificate, again the encoding could be PEM or DER; a certificate contains the public key, but it contains much more information (most importantly the signature by the Certificate Authority over the data and public key, of course).
- How exactly would I generate a.key file and a.crt file from a.p12 file? Stack Exchange Network Stack Exchange network consists of 175 Q&A communities including Stack Overflow, the largest, most trusted online community for developers to learn.
Howto convert a PFX to a seperate.key/.crt file. In some cases you might be forced to convert your private key to PEM format. You can do so with the following command: openssl rsa -in keyfile-encrypted.key -outform PEM -out keyfile-encrypted-pem.key. I’ve used it to generate a key file for my Synology NAS. Reply this message.
commented Jul 18, 2015
How To Generate Pem File From Crt
Thx! |
commented Sep 17, 2015
thank you so much... u save me.. |
commented Jan 26, 2018
you have 'hsot' name in your code. If you cut and paste this, make sure you correct the type or you're not going to get too far. |
commented Jul 12, 2018
perfect!!! |
commented Aug 22, 2018
Thanks, forgot how to convert private keys when setting up a mysql instance. Second method worked perfectly |
Pem To Crt
commented Jan 15, 2019
the command generate an empty file, any idea please? |
commented Jul 30, 2019
You king. Thanks for the help! |

commented Jul 30, 2019
Wow, I'd completely forgotten about this snippet. I'm glad to see it's been helpful to someone besides myself. |
.pem SSL Creation Instructions

SSL .pem files (concatenated certificate container files), are frequently required for certificate installations when multiple certificates are being imported as one file.
This article contains multiple sets of instructions that walk through various .pem file creation scenarios.
Creating a .pem with the Entire SSL Certificate Trust Chain
- Log into your DigiCert Management Console and download your Intermediate (DigiCertCA.crt), Root (TrustedRoot.crt), and Primary Certificates (your_domain_name.crt).
Open a text editor (such as wordpad) and paste the entire body of each certificate into one text file in the following order:
- The Primary Certificate - your_domain_name.crt
- The Intermediate Certificate - DigiCertCA.crt
- The Root Certificate - TrustedRoot.crt
Make sure to include the beginning and end tags on each certificate. The result should look like this:
-----BEGIN CERTIFICATE-----
(Your Primary SSL certificate: your_domain_name.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Intermediate certificate: DigiCertCA.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Root certificate: TrustedRoot.crt)
-----END CERTIFICATE-----Save the combined file as your_domain_name.pem. The .pem file is now ready to use.
Creating a .pem with the Server and Intermediate Certificates
- Log into your DigiCert Management Console and download your Intermediate (DigiCertCA.crt) and Primary Certificates (your_domain_name.crt).
Open a text editor (such as wordpad) and paste the entire body of each certificate into one text file in the following order:
- The Primary Certificate - your_domain_name.crt
- The Intermediate Certificate - DigiCertCA.crt
Make sure to include the beginning and end tags on each certificate. The result should look like this:
-----BEGIN CERTIFICATE-----
(Your Primary SSL certificate: your_domain_name.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Intermediate certificate: DigiCertCA.crt)
-----END CERTIFICATE-----Save the combined file as your_domain_name.pem. The .pem file is now ready to use.
Creating a .pem with the Private Key and Entire Trust Chain
- Log into your DigiCert Management Console and download your Intermediate (DigiCertCA.crt) and Primary Certificates (your_domain_name.crt).
Open a text editor (such as wordpad) and paste the entire body of each certificate into one text file in the following order:
- The Private Key - your_domain_name.key
- The Primary Certificate - your_domain_name.crt
- The Intermediate Certificate - DigiCertCA.crt
- The Root Certificate - TrustedRoot.crt
Make sure to include the beginning and end tags on each certificate. The result should look like this:
-----BEGIN RSA PRIVATE KEY-----
(Your Private Key: your_domain_name.key)
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
(Your Primary SSL certificate: your_domain_name.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Intermediate certificate: DigiCertCA.crt)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Your Root certificate: TrustedRoot.crt)
-----END CERTIFICATE-----Save the combined file as your_domain_name.pem. The .pem file is now ready to use.

Windows Server 2016 Essentials Key Generator

- Windows Server 2016 Essentials Key Generator Software
- Windows Server 2016 Essentials Key Generator Replacement
- Windows Server 2016 Essentials Key Generator Manual
All of the examples provided are installation keys only; they will not activate your installed version of Windows. They are the default keys that are inserted if you choose to skip entering a Product Key during the installation process.
This server has much built-in functionality, so you do not have to install extra tools. Windows Server 2016 Keygen With All Keys Here: Furthermore, Microsoft released 4 version of this newest OS to operate overall usage of operating system such as Windows Server 2016, Windows Server 2016 Hyper-V and Windows Server 2016 Essentials.
Windows Server 2016 Essentials Key Generator Software
Windows Server 2016 Essentials Key Generator Replacement
The product keys listed in this section can be used with any of the answer files and scripted examples. They are blocked at the Microsoft clearinghouse and therefore cannot be used to activate any systems. They provide a number of days for you to complete the activation process. The keys supplied are not architecture dependent.
Windows Server 2016 Essentials Key Generator Manual
It is absolutely essential that you use the correct type of key, which is a function of the edition type. Choose the key corresponding to which edition of Windows you wish to install.
| Windows Edition | Product Key |
| Windows Vista Starter | X9PYV-YBQRV-9BXWV-TQDMK-QDWK4 |
| Windows Vista Home Basic | RCG7P-TX42D-HM8FM-TCFCW-3V4VD |
| Windows Vista Home Premium | X9HTF-MKJQQ-XK376-TJ7T4-76PKF |
| Windows Vista Business | 4D2XH-PRBMM-8Q22B-K8BM3-MRW4W |
| Windows Vista Ultimate | VMCB9-FDRV6-6CDQM-RV23K-RP8F7 |
| Windows 7 Starter | 7Q28W-FT9PC-CMMYT-WHMY2-89M6G |
| Windows 7 Home Basic | YGFVB-QTFXQ-3H233-PTWTJ-YRYRV |
| Windows 7 Home Premium | RHPQ2-RMFJH-74XYM-BH4JX-XM76F |
| Windows 7 Professional | HYF8J-CVRMY-CM74G-RPHKF-PW487 |
| Windows 7 Ultimate | D4F6K-QK3RD-TMVMJ-BBMRX-3MBMV |
| Windows 7 Enterprise | H7X92-3VPBB-Q799D-Y6JJ3-86WC6 |
| Windows 7 Starter N | D4C3G-38HGY-HGQCV-QCWR8-97FFR |
| Windows 7 Home Basic N | MD83G-H98CG-DXPYQ-Q8GCR-HM8X2 |
| Windows 7 Home Premium N | D3PVQ-V7M4J-9Q9K3-GG4K3-F99JM |
| Windows 7 Professional N | BKFRB-RTCT3-9HW44-FX3X8-M48M6 |
| Windows 7 Ultimate N | HTJK6-DXX8T-TVCR6-KDG67-97J8Q |
| Windows 7 Enterprise N | BQ4TH-BWRRY-424Y9-7PQX2-B4WBD |
| Windows 7 Starter E | BRQCV-K7HGQ-CKXP6-2XP7K-F233B |
| Windows 7 Home Basic E | VTKM9-74GQY-K3W94-47DHV-FTXJY |
| Windows 7 Home Premium E | 76BRM-9Q4K3-QDJ48-FH4F3-9WT2R |
| Windows 7 Professional E | 3YHKG-DVQ27-RYRBX-JMPVM-WG38T |
| Windows 7 Ultimate E | TWMF7-M387V-XKW4Y-PVQQD-RK7C8 |
| Windows 7 Enterprise E | H3V6Q-JKQJG-GKVK3-FDDRF-TCKVR |
| Windows 8 | FB4WR-32NVD-4RW79-XQFWH-CYQG3 |
| Windows 8 (ARM) | 6D4CN-WMGRW-DG8M6-XX8W9-3RPT8 |
| Windows 8 (Country Specific) | XYNVP-TW798-F8893-7B89K-8QHDK |
| Windows 8 (Single Language) | XBRND-QDJTG-CQJDB-7DRBW-RX6HB |
| Windows 8 Professional | XKY4K-2NRWR-8F6P2-448RF-CRYQH |
| Windows 8 Professional with WMC | RR3BN-3YY9P-9D7FC-7J4YF-QGJXW |
| Windows 8 Enterprise | 32JNW-9KQ84-P47T8-D8GGY-CWCK7 |
| Windows 8 N | VDKYM-JNKJ7-DC4X9-BT3QR-JHRDC |
| Windows 8 Professional N | BHHD4-FKNK8-89X83-HTGM4-3C73G |
| Windows 8 Enterprise N | NCVKH-RB9D4-R86X8-GB8WG-4M2K6 |
| Windows 8.1 | 334NH-RXG76-64THK-C7CKG-D3VPT |
| Windows 8.1 (ARM) | NK2V7-9DWXG-KMTWQ-K9H9M-6VHPJ |
| Windows 8.1 (Country Specific) | TNH8J-KG84C-TRMG4-FFD7J-VH4WX |
| Windows 8.1 (Single Language) | Y9NXP-XT8MV-PT9TG-97CT3-9D6TC |
| Windows 8.1 Professional | GCRJD-8NW9H-F2CDX-CCM8D-9D6T9 |
| Windows 8.1 Professional with WMC | GBFNG-2X3TC-8R27F-RMKYB-JK7QT |
| Windows 8.1 Enterprise | FHQNR-XYXYC-8PMHT-TV4PH-DRQ3H |
| Windows 8.1 N | 6NPQ8-PK64X-W4WMM-MF84V-RGB89 |
| Windows 8.1 Professional N | JRBBN-4Q997-H4RM2-H3B7W-Q68KC |
| Windows 8.1 Enterprise N | NDRDJ-3YBP2-8WTKD-CK7VB-HT8KW |
| Windows 10 Home | TX9XD-98N7V-6WMQ6-BX7FG-H8Q99 |
| Windows 10 Pro | W269N-WFGWX-YVC9B-4J6C9-T83GX |
| Windows 10 Education | NW6C2-QMPVW-D7KKK-3GKT6-VCFB2 |
| Windows 10 Enterprise | NPPR9-FWDCX-D2C8J-H872K-2YT43 |
| Windows Server 2008 Standard | TM24T-X9RMF-VWXK6-X8JC9-BFGM2 |
| Windows Server 2008 Web | WYR28-R7TFJ-3X2YQ-YCY4H-M249D |
| Windows Server 2008 HPC | RCTX3-KWVHP-BR6TB-RB6DM-6X7HP |
| Windows Server 2008 Enterprise | YQGMW-MPWTJ-34KDK-48M3W-X4Q6V |
| Windows Server 2008 Itanium | 7YKJ4-CX8QP-Q23QY-7BYQM-H2893 |
| Windows Server 2008 Datacenter | 7M67G-PC374-GR742-YH8V4-TCBY3 |
| Windows SBS 2008 Standard | PHYFD-HQ4XW-78PR4-2CXKF-V67KJ |
| Windows SBS 2008 Premium | 4TMY4-8JG4B-VKY8X-6TVDH-J7XFV |
| Windows Server 2008 R2 Foundation | 36RXV-4Y4PJ-B7DWH-XY4VW-KQXDQ |
| Windows Server 2008 R2 Standard | YC6KT-GKW9T-YTKYR-T4X34-R7VHC |
| Windows Server 2008 R2 Web | 6TPJF-RBVHG-WBW2R-86QPH-6RTM4 |
| Windows Server 2008 R2 HPC | TT8MH-CG224-D3D7Q-498W2-9QCTX |
| Windows Server 2008 R2 Enterprise | 489J6-VHDMP-X63PK-3K798-CPX3Y |
| Windows Server 2008 R2 Itanium | GT63C-RJFQ3-4GMB6-BRFB9-CB83V |
| Windows Server 2008 R2 Datacenter | 74YFP-3QFB3-KQT8W-PMXWJ-7M648 |
| Windows Hyper-V Server 2008 R2 | Q8R8C-T2W6H-7MGPB-4CQ9R-KR36H |
| Windows MultiPoint Server 2010 | 736RG-XDKJK-V34PF-BHK87-J6X3K |
| Windows SBS 2011 Standard | YT76W-VD3W9-QDCK4-9QFPX-WQY4J |
| Windows SBS 2011 Premium | BXQQP-Q6Q6D-TR7TR-3YXQW-VFHKM |
| Windows Home Server 2011 Standard | BTMWJ-8KHD9-B9BX8-J7JQ9-7M6J2 |
| Windows Home Server 2011 Premium | YQXDR-G2MBV-63VW2-JX8J2-FVTVG |
| Windows Server 2012 Foundation | PN24B-X6THG-274MF-YHM9G-H8MVG |
| Windows Server 2012 Standard | VN93G-8PVT3-W2X3H-F3X87-FJMTW |
| Windows Server 2012 Datacenter | 2GMNX-8K7D2-X968C-7P62F-8B2QK |
| Windows Server 2012 Storage Server | RD9XF-6N3MC-2P2R3-MK2WX-C7GCW |
| Windows Multipoint Server 2012 Standard | 32TNQ-HMFWQ-8R933-X6VYY-WHRFX |
| Windows Multipoint Server 2012 Premium | CBR2N-2HG39-2TGGT-GQB27-46V47; |
| Windows Server 2012 Standard Core | VN93G-8PVT3-W2X3H-F3X87-FJMTW |
| Windows Server 2012 Datacenter Core | 2GMNX-8K7D2-X968C-7P62F-8B2QK |
| Windows Server 2012 R2 Essentials | KNC87-3J2TX-XB4WP-VCPJV-M4FWM |
| Windows Server 2012 R2 Foundation | 7JGXN-BW8X3-DTJCK-WG7XB-YWP26 |
| Windows Server 2012 R2 Standard | D2N9P-3P6X9-2R39C-7RTCD-MDVJX |
| Windows Server 2012 R2 Datacenter | W3GGN-FT8W3-Y4M27-J84CP-Q3VJ9 |
| Windows Server 2012 R2 Storage Server Standard | H2K4M-QNKQ2-64699-FYQHD-2WDYT |
| Windows Server 2012 R2 Storage Server Workgroup | 8N7PM-D3C64-RQVYF-MX8T7-G6MB2 |
| Microsoft Hyper-V Server 2012 R2 | Q8R8C-T2W6H-7MGPB-4CQ9R-KR36H |
| Windows Server 2012 R2 Essentials Core | 326N4-6GMBX-PD2QT-M7HX4-TVHM8 |
| Windows Server 2012 R2 Foundation Core | 7JGXN-BW8X3-DTJCK-WG7XB-YWP26 |
| Windows Server 2012 R2 Standard Core | NB4WH-BBBYV-3MPPC-9RCMV-46XCB |
| Windows Server 2012 R2 Datacenter Core | BH9T4-4N7CW-67J3M-64J36-WW98Y |
| Windows Server 2012 R2 Storage Server Standard Core | H2K4M-QNKQ2-64699-FYQHD-2WDYT |
| Windows Server 2012 R2 Storage Server Workgroup Core | 8N7PM-D3C64-RQVYF-MX8T7-G6MB2 |
| Windows Server 2016 Essentials | JCKRF-N37P4-C2D82-9YXRT-4M63B |
| Windows Server 2016 Standard | WC2BQ-8NRM3-FDDYY-2BFGV-KHKQY |
| Windows Server 2016 Datacenter | CB7KF-BWN84-R7R2Y-793K2-8XDDG |
| Windows Server 2019 Standard | N69G4-B89J2-4G8F4-WWYCC-J464C |
| Windows Server 2019 Datacenter | WMDGN-G9PQG-XVVXX-R3X43-63DFG |
Mar 28, 2020 System Requirements for Windows Server 2016: Your system must be 64-bit. 4 GHz would work, however, 3.1 GHz is recommended. 2 GB of RAM can run Windows Server 2016 key applied OS. Mar 15, 2018 If you have Server 2016 Data Center your server likely came with a single COA (Certificate of Authenticity) sticker containing a single DataCenter CD Key. If you then try to use that Key to activate new Server 2016 or Server 2012 Standard VM’s it will fail.

Generate New Django Secret Key

Mar 12, 2012 How to generate a secret key with Python. GitHub Gist: instantly share code, notes, and snippets. How to use sessions¶ Django provides full support for anonymous sessions. The session framework lets you store and retrieve arbitrary data on a per-site-visitor basis. An attacker in possession of the SECRETKEY can not only generate falsified session data, which your site will trust. Creates a new session key while retaining the.
Source code:Lib/secrets.py
The secrets module is used for generating cryptographically strongrandom numbers suitable for managing data such as passwords, accountauthentication, security tokens, and related secrets.
In particularly, secrets should be used in preference to thedefault pseudo-random number generator in the random module, whichis designed for modelling and simulation, not security or cryptography.
See also
PEP 506
Random numbers¶
The secrets module provides access to the most secure source ofrandomness that your operating system provides.
secrets.SystemRandom¶A class for generating random numbers using the highest-qualitysources provided by the operating system. Seerandom.SystemRandom for additional details.
secrets.choice(sequence)¶
Return a randomly-chosen element from a non-empty sequence.
secrets.randbelow(n)¶Return a random int in the range [0, n).
secrets.randbits(k)¶Return an int with k random bits.
Generating tokens¶
The secrets module provides functions for generating securetokens, suitable for applications such as password resets,hard-to-guess URLs, and similar.
secrets.token_bytes([nbytes=None])¶Return a random byte string containing nbytes number of bytes.If nbytes is None or not supplied, a reasonable default isused.
secrets.token_hex([nbytes=None])¶Return a random text string, in hexadecimal. The string has nbytesrandom bytes, each byte converted to two hex digits. If nbytes isNone or not supplied, a reasonable default is used.
secrets.token_urlsafe([nbytes=None])¶Return a random URL-safe text string, containing nbytes randombytes. The text is Base64 encoded, so on average each byte resultsin approximately 1.3 characters. If nbytes is None or notsupplied, a reasonable default is used.
How many bytes should tokens use?¶
To be secure againstbrute-force attacks,tokens need to have sufficient randomness. Unfortunately, what isconsidered sufficient will necessarily increase as computers get morepowerful and able to make more guesses in a shorter period. As of 2015,it is believed that 32 bytes (256 bits) of randomness is sufficient forthe typical use-case expected for the secrets module.
For those who want to manage their own token length, you can explicitlyspecify how much randomness is used for tokens by giving an intargument to the various token_* functions. That argument is takenas the number of bytes of randomness to use.
Otherwise, if no argument is provided, or if the argument is None,the token_* functions will use a reasonable default instead.
Note
That default is subject to change at any time, including duringmaintenance releases.

Other functions¶
secrets.compare_digest(a, b)¶Return True if strings a and b are equal, otherwise False,in such a way as to reduce the risk oftiming attacks.See hmac.compare_digest() for additional details.
Recipes and best practices¶
This section shows recipes and best practices for using secretsto manage a basic level of security.
Generate an eight-character alphanumeric password:
Note
Applications should notstore passwords in a recoverable format,whether plain text or encrypted. They should be salted and hashedusing a cryptographically-strong one-way (irreversible) hash function.
Generate a ten-character alphanumeric password with at least onelowercase character, at least one uppercase character, and at leastthree digits:
Generate an XKCD-style passphrase:
Generate a hard-to-guess temporary URL containing a security tokensuitable for password recovery applications:
Generate New Django Secret Key West
Simple Django application that adds a new command:
This will generate a new file secretkey.txt containing a random Django secretkey. In your production settings file, replace the hardcoded key by:
You can avoid hardcoding the path of the key by using:
Install
You can install this package from PyPi:
Then you will need to add it to the Django's INSTALLED_APPS setting:
Generate New Django Secret Key West
You can now use
Run this command once in your local environment, and every time you deploy your app (on the remote host), to make sure the file exists.
